You need to ensure that User2 can implement PIM.
What should you do first?
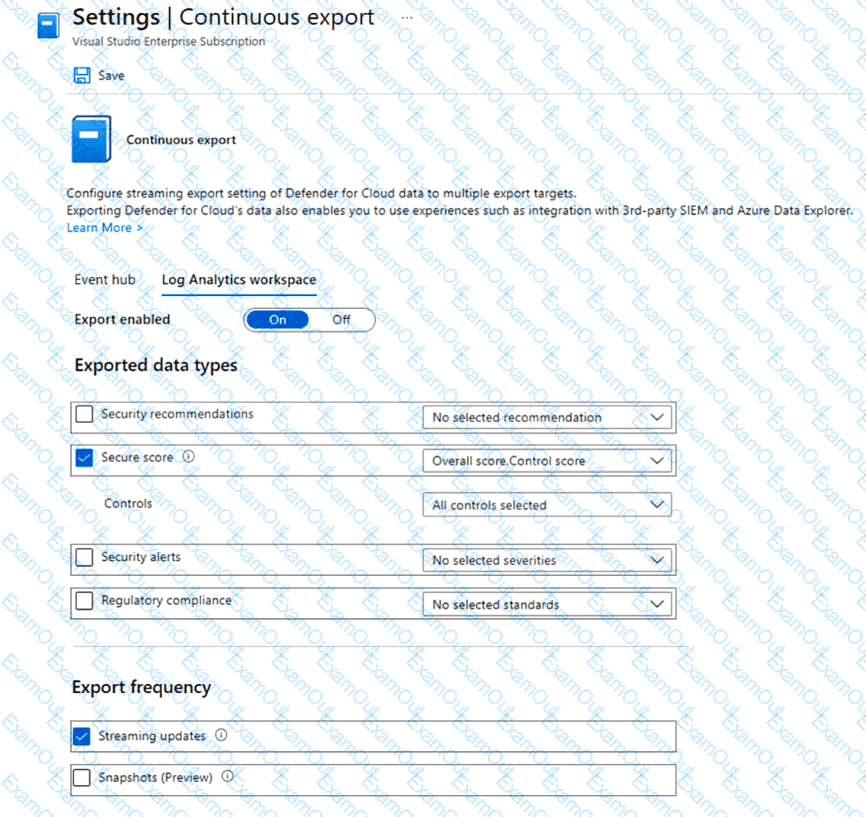
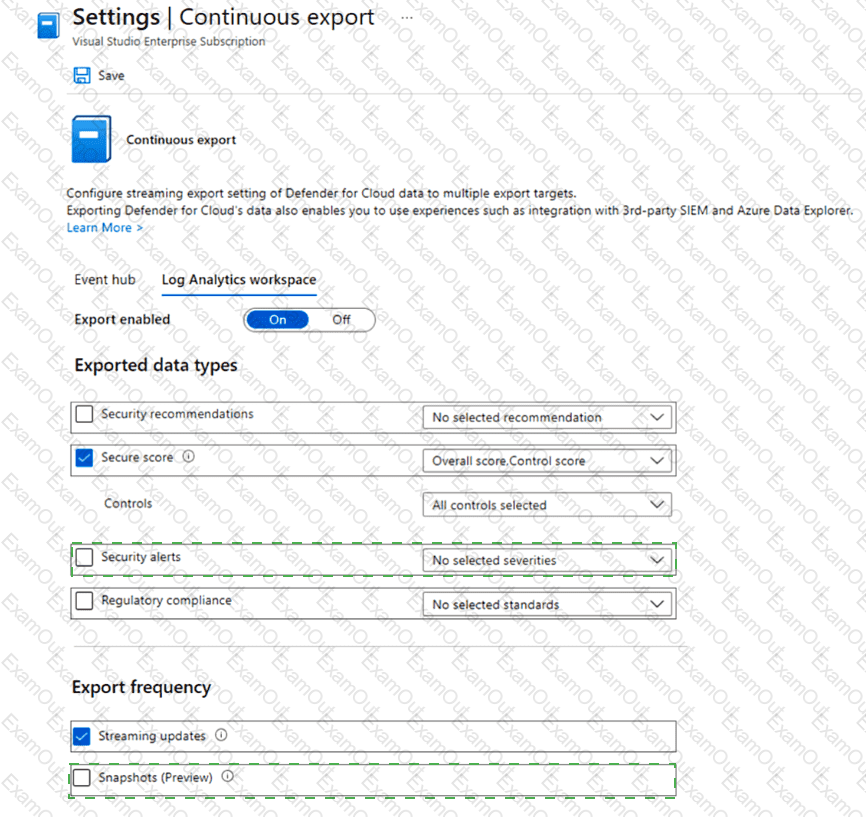
You have an Azure subscription that uses Microsoft Defender for Cloud.
You plan to use the Secure Score Over Time workbook.
You need to configure the Continuous export settings for the Defender for Cloud data.
Which two settings should you configure? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
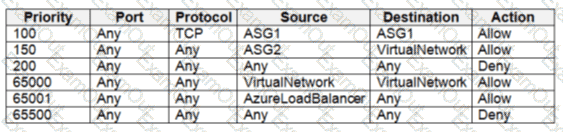
You need to meet the technical requirements for VNetwork1.
What should you do first?
You have an Azure SQL Database server named SQL1.
You plan to turn on Advanced Threat Protection for SQL1 to detect all threat detection types.
Which action will Advanced Threat Protection detect as a threat?
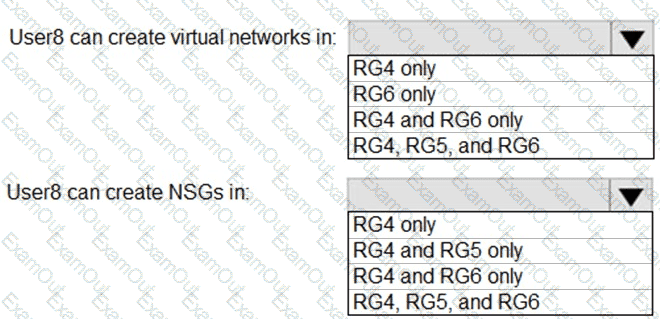
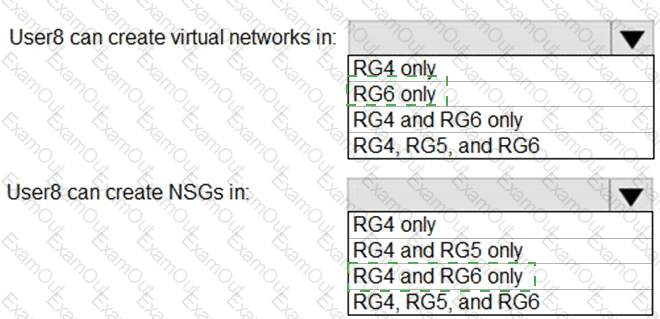
You assign User8 the Owner role for RG4, RG5, and RG6.
In which resource groups can User8 create virtual networks and NSGs? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
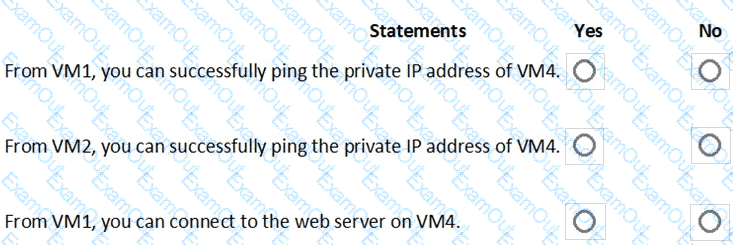
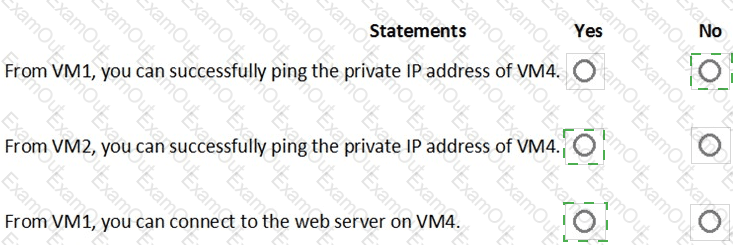
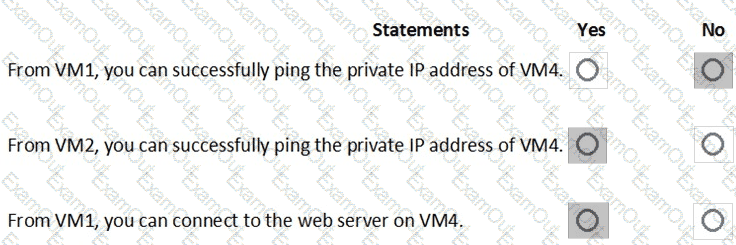
You are evaluating the effect of the application security groups on the network communication between the virtual machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
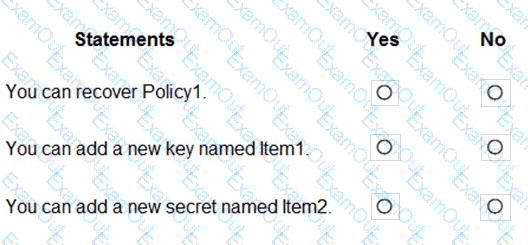
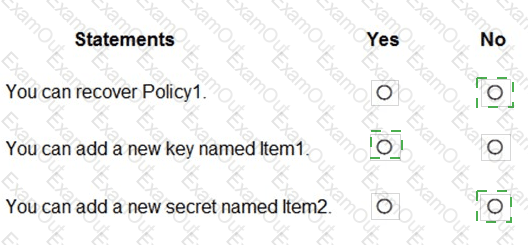
You have an Azure key vault named KeyVault1 that contains the items shown in the following table.

In KeyVault, the following events occur in sequence:
Item1 is deleted
Administrator enables soft delete
Item2 and Policy1 are deleted.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains an Azure key vault.
You need to configure maximum number of days for Which new keys are valid. The solution must minimize administrative effort.
What should you use?
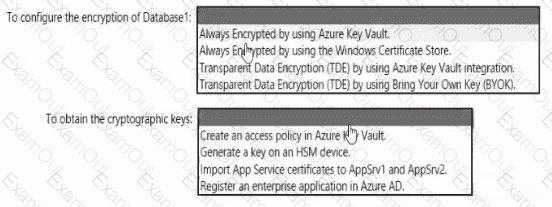
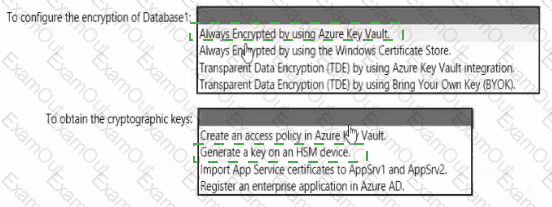
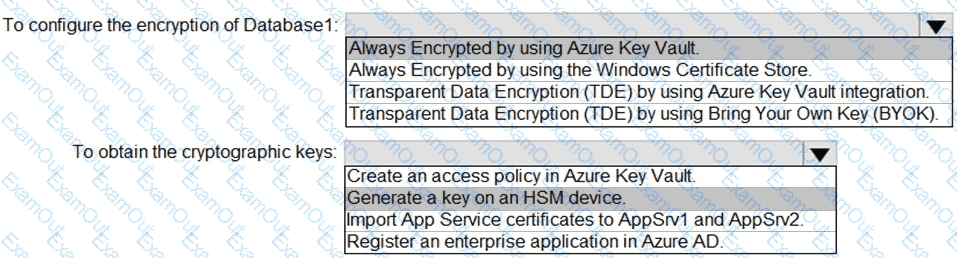
You have an Azure subscription that contains the following resources:
• An Azure key vault
• An Azure SQL database named Database1
• Two Azure App Service web apps named AppSrv1 and AppSrv2 that are configured to use system-assigned managed identities and access Database1
You need to implement an encryption solution for Database1 that meets the following requirements:
• The data in a column named Discount in Database1 must be encrypted so that only AppSrv1 can decrypt the data.
• AppSrv1 and AppSrv2 must be authorized by using managed identities to obtain cryptographic keys.
How should you configure the encryption settings fa Database1 To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point
You have an Azure subscription that is linked to an Azure AD tenant and contains the resources shown in the following table.
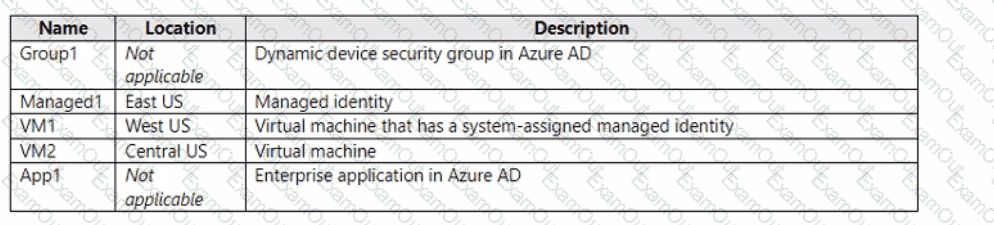
Which resources can be assigned the Contributor role for VM1?

 Text Description automatically generated with medium confidence
Text Description automatically generated with medium confidence