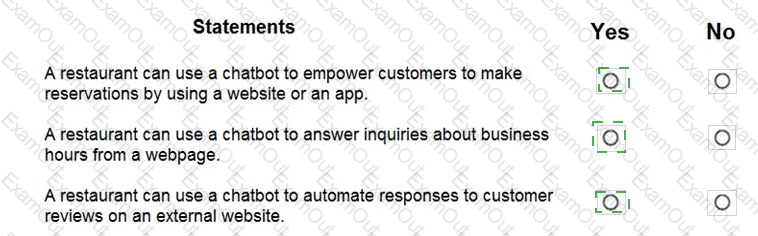
You have the Predicted vs. True chart shown in the following exhibit.
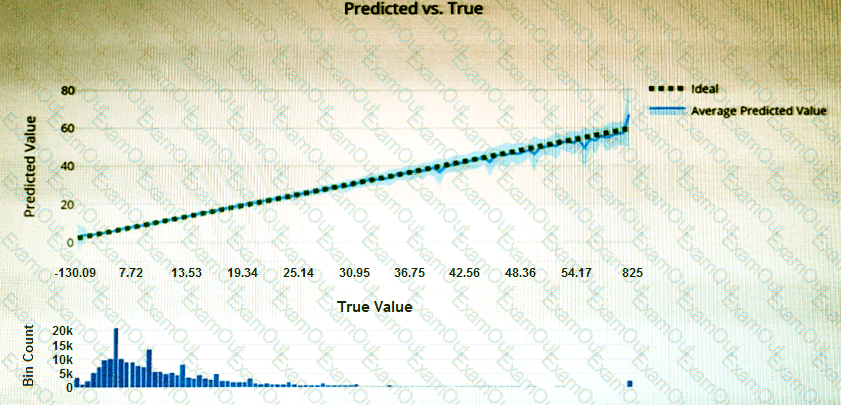
Which type of model is the chart used to evaluate?
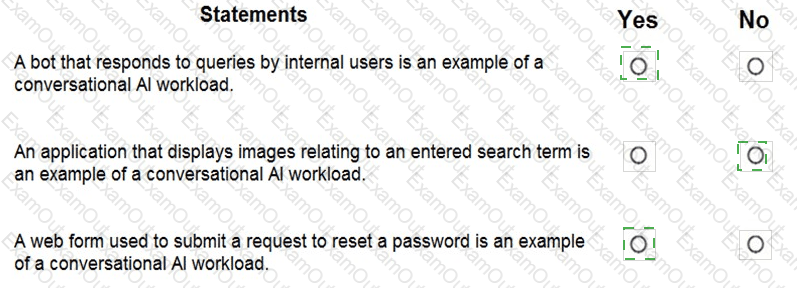
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
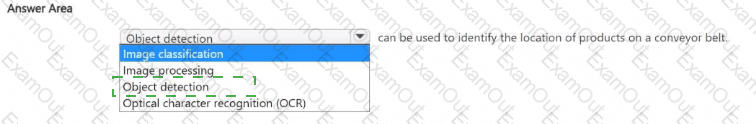
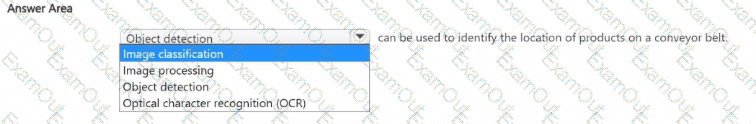
Select the answer that correctly completes the sentence.
You are designing a system that will generate insurance quotes automatically.
Match the Microsoft responsible Al principles to the appropriate requirements.
To answer, drag the appropriate principle from the column on the left to its requirement on the right Each principle may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.

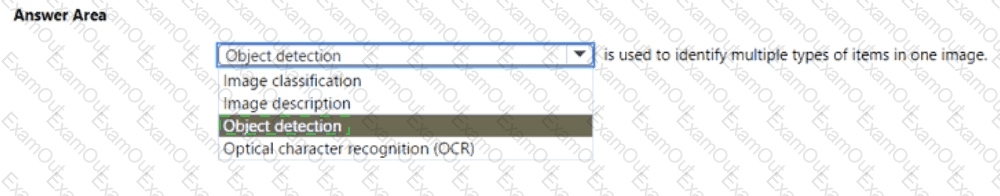
Select the answer that correctly completes the sentence
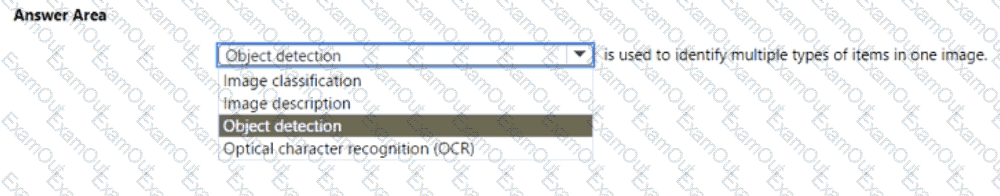
You have a dataset that contains experimental data for fuel samples.
You need to predict the amount of energy that can be obtained from a sample based on its density.
Which type of Al workload should you use?
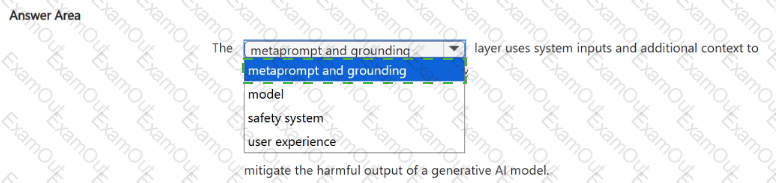
Select the answer that correctly completes the sentence.
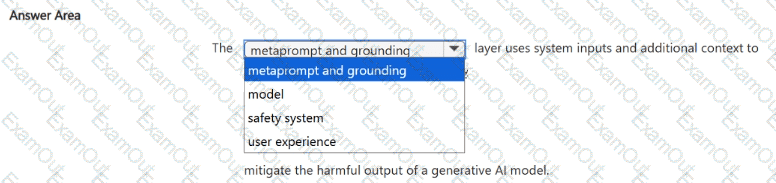
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You are developing a natural language processing solution in Azure. The solution will analyze customer reviews and determine how positive or negative each review is.
This is an example of which type of natural language processing workload?
What is an example of the Microsoft responsible Al principle of transparency?