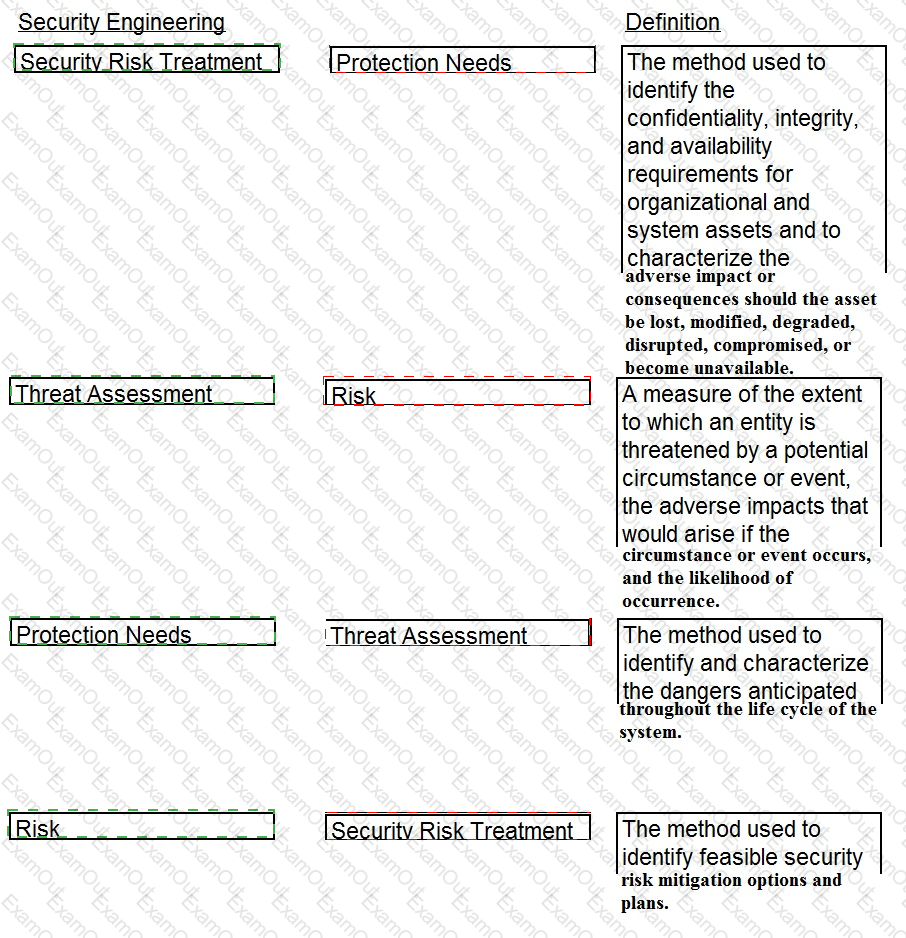
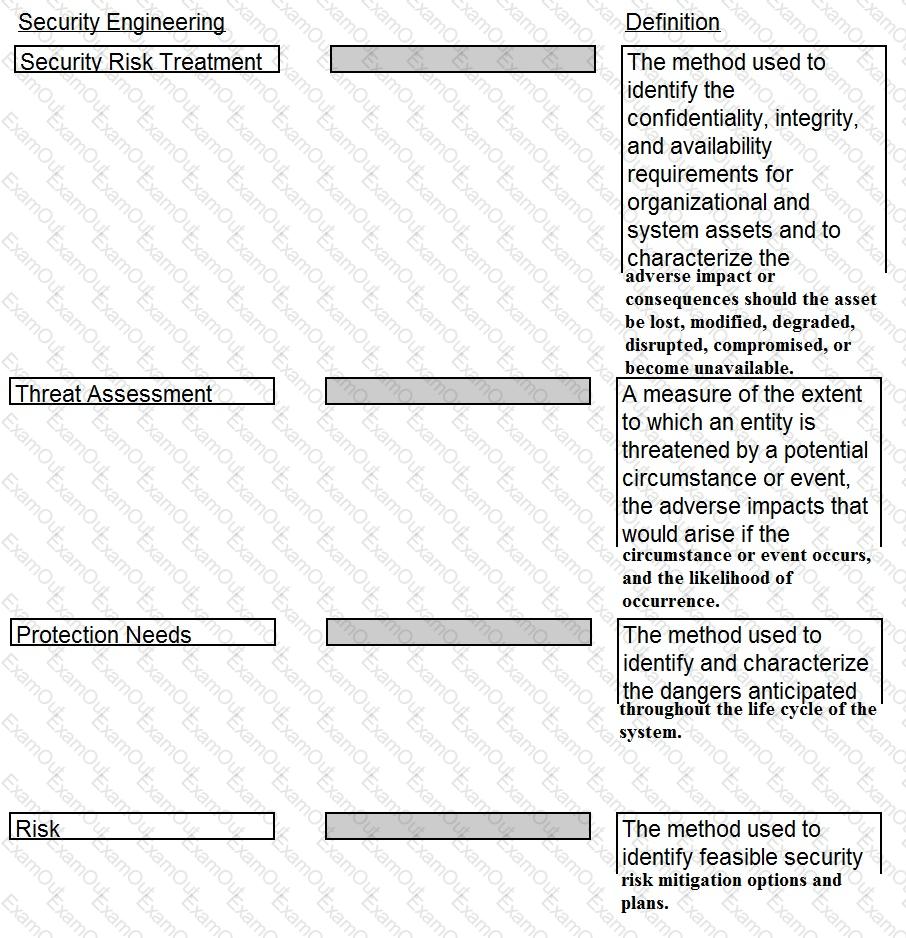
Drag the following Security Engineering terms on the left to the BEST definition on the right.
Which of the following roles has the obligation to ensure that a third party provider is capable of processing and handling data in a secure manner and meeting the standards set by the organization?
In which identity management process is the subject’s identity established?
The BEST example of the concept of "something that a user has" when providing an authorized user access to a computing system is
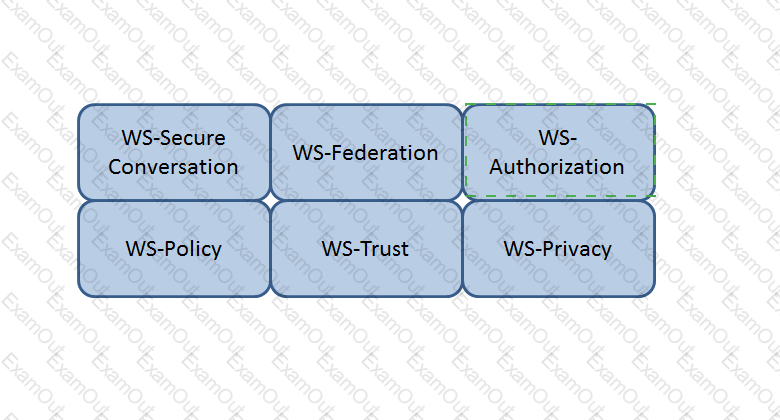
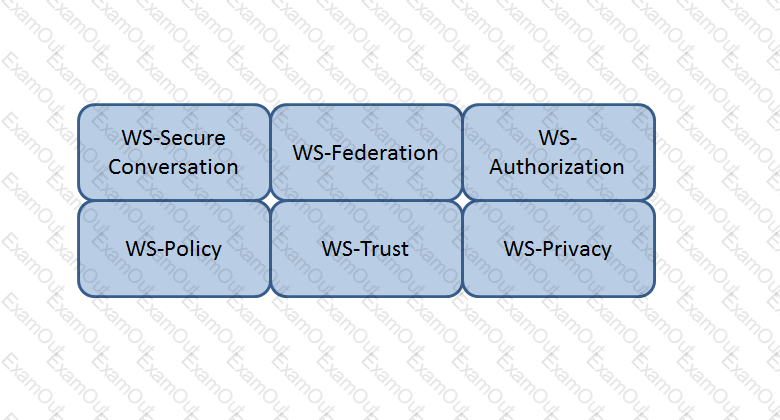
Which Web Services Security (WS-Security) specification handles the management of security tokens and the underlying policies for granting access? Click on the correct specification in the image below.
How does Encapsulating Security Payload (ESP) in transport mode affect the Internet Protocol (IP)?
Which of the following methods can be used to achieve confidentiality and integrity for data in transit?
By carefully aligning the pins in the lock, which of the following defines the opening of a mechanical lock without the proper key?
Which of the following approaches is the MOST effective way to dispose of data on multiple hard drives?
What is the PRIMARY difference between security policies and security procedures?
The restoration priorities of a Disaster Recovery Plan (DRP) are based on which of the following documents?
Which of the following is the BIGGEST weakness when using native Lightweight Directory Access Protocol (LDAP) for authentication?
Which of the following prevents improper aggregation of privileges in Role Based Access Control (RBAC)?
In the Open System Interconnection (OSI) model, which layer is responsible for the transmission of binary data over a communications network?
During the Security Assessment and Authorization process, what is the PRIMARY purpose for conducting a hardware and software inventory?