A hacker gains access to a compony network and begins to intercept network traffic in order to steal login credentials which OSI layer is being attacked
Which of the following is not a protocol of the OSI layer 3
Which of these activities is often associated with DR efforts?
Government can imposes financial penalties as a consequence of breaking a
Exhibit.
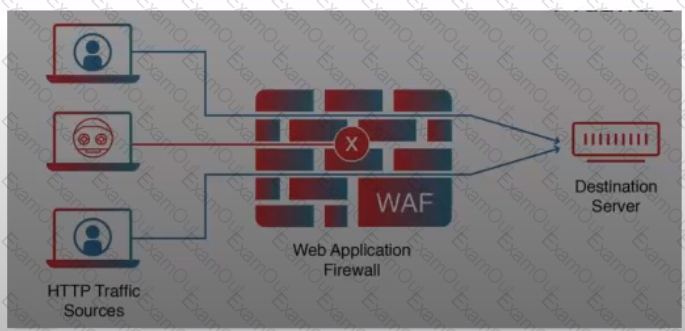
What is the PRIMARY purpose of a web application firewall (WAF)?
What is the benefit of subnet
An external entity has tried to gain access to your organization's IT environment without proper authorization. This is an example of a(n)
Who should participate in creation a business continuity plan
Which of the following documents contains elements that are NOT mandatory
A standard that defines wired communications of network devices

