A carrier's home broadband service requires a maximum downstream bandwidth of 100 Mbit/s during off-peak hours and a guaranteed downstream bandwidth of 50 Mbit/s during peak hours. The home broadband service includes the home IP phone service and the home Internet access service. Which of the following configurations best meets the service requirement?
Which of the following are advantages of GRE tunnels? (Select All that Apply)
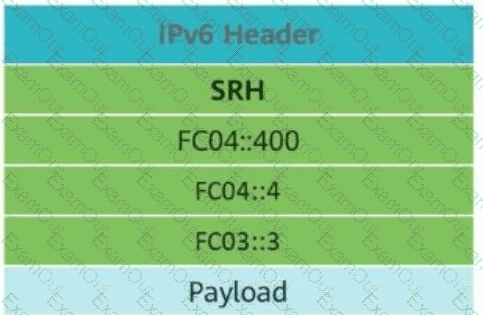
This figure shows anSRv6 (Segment Routing over IPv6)packet. If theDestination Addressfield in the IPv6 basic header isFC04::4, the value of theSL (Segment Left)field in the SRv6 header should be____.(Enter only digits.)
Which of the following statements is incorrect about Authentication Header (AH)?
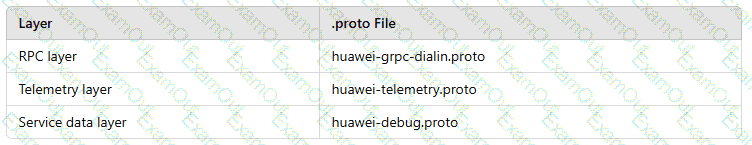
In the gRPC-based telemetry protocol, the data model layer consists of theRPC layer,telemetry layer, andservice data layer. Drag the.proto fileto the layer where the file should be located.
The following information is displayed during OSPF troubleshooting. Based on this information, which of the following is the cause of the failure in establishing an OSPF adjacency relationship?
OSPF Process 1 with Router ID 10.0.12.2
OSPF error statistics
Interface: GigabitEthernet0/0/0 (10.0.12.2)
General packet errors:
0 : Bad version 0 : Bad checksum
0 : Bad area id 0 : Bad authentication type
0 : Bad authentication key 0 : Unknown neighbor
0 : Bad net segment 0 : Extern option mismatch
0 : Router id confusion
HELLO packet errors:
2 : Netmask mismatch 0 : Hello timer mismatch
0 : Dead timer mismatch 0 : Invalid Source Address
Which of the following is the mapping between VNIs and BDs in VXLAN implementation?
Which of the following statements is incorrect about the user authentication points on the network?
Which of the following commands needs to be run in the BGP view to enable a VPN instance to advertise IP routes to the BGP-EVPN address family?
Which of the following technologies can be used to isolate users in the same VLAN?

 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.