An OSPF AS-external LSA describes a route to an AS external network. When the field in the LSA is 0.0.0.0, the traffic destined for the external network is sent to the ASBR that imports this external route. (Enter the acronym in uppercase.)
On an IPv6 network, intermediate forwarding devices do not fragment IPv6 packets for the purpose of reducing their packet processing pressure. Packets are fragmented only on the source node.
In IPv6, interface IDs can be manually configured, automatically generated by the system, or generated based on the IEEE EUI-64 standard.
Typically, a protocol that occupies two ports during communication is called a multi-channel protocol. For such protocols, the ASPF function must be enabled on the firewall to ensure smooth setup of the data channel and reduce the risk of attacks. Which of the following protocols is not a multi-channel protocol?
After which of the following parameters are modified does an IS-IS neighbor relationship need to re-established?
Which of the following attributes must be carried when BGP sends route update messages?
ON a stateful inspection Firewall where there is no session table, when the status detection mechanism is enabled and the second packet (CYN+ACK) of 3-way hadshakes reaches the firewall. Which of the following statements is true?
The BFD Echo function checks the connectivity of the forwarding link by looping back packets. Which of the following statements are true about this function?
On an IS-IS network, each router can generate LSPs. Which of the following events trigger the generation of a new LSP?
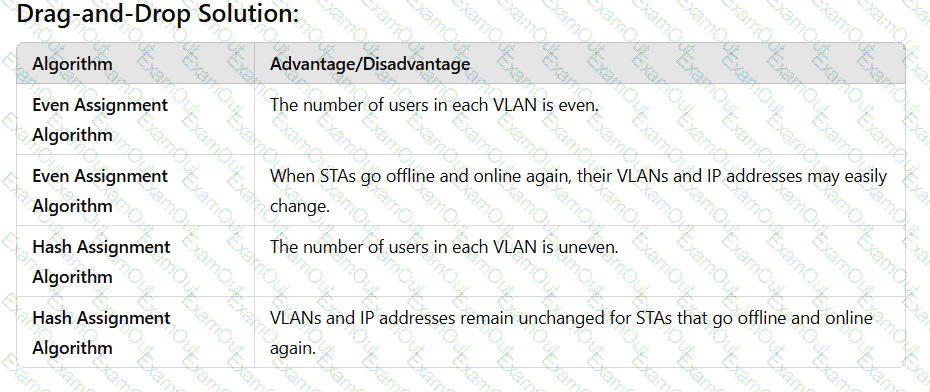
On a WLAN, engineers can use the VLAN pool mechanism to assign access users to different VLANs, which helps reduce the number of broadcast domains and improve network performance. VLAN pools support two VLAN assignment algorithms: even and hash. Drag the advantages and disadvantages to the two algorithms.(Token is reusable)

 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated