The TCP protocol uses the three-way handshake mechanism to establish and disable connections. Therefore, TCP supports reliable data transmission.
Refer to the display startup command output shown in the figure. Which of the following statements are true?
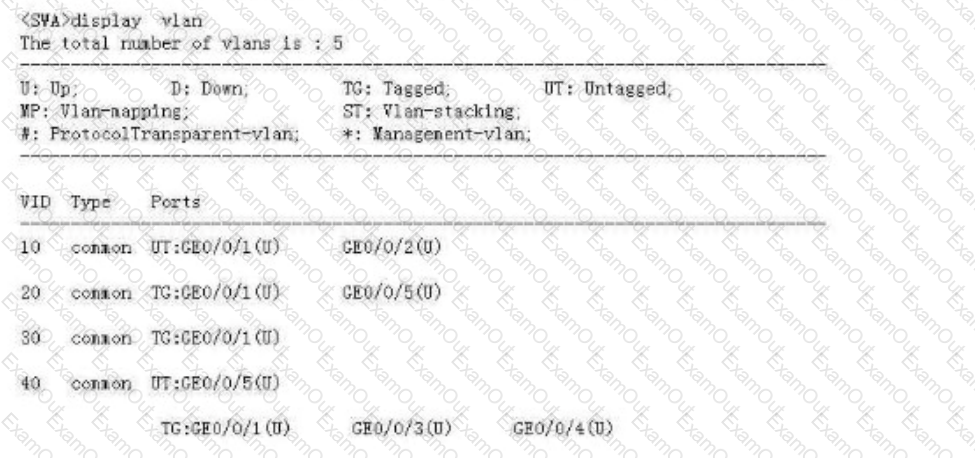
Refer to the following display vlan command output on SWA. Which of the following interfaces can forward untagged data frames from VLAN 40?
By referring to the topology and the configurations of G0/0/1 interfaces on LSW1 and LSW2 shown in the figure, it can be determined that data frames tagged with VLAN 10 can be normally forwarded between LSW1 and LSW2.
Which of the following is correct regarding the configuration of the trunk port and access port on a switch?
Refer to the following configuration of an interface on a switch. For which VLAN does the interface remove VLAN tags before forwarding data frames?
go
CopyEdit
interface GigabitEthernet0/0/1
port link-type trunk
port trunk pvid vlan 10
port trunk allow-pass vlan 10 20 30 40
Which of the following frequency bands are supported by IEEE 802.11n?
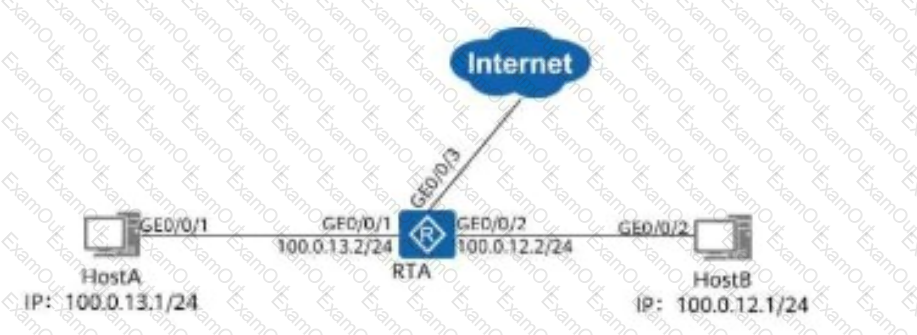
Which of the following configurations can prevent Host A and Host B from communicating with each other?
To enable Router A to communicate with Loopback 0 on Router B on the network shown in the figure, which of the following commands needs to be run on Router A?

After the administrator performs the configuration shown in the figure on a router, which of the following commands can be used to specify a short lease for addresses assigned using DHCP?

