A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as a TACACS+ server to authenticate managers on its AOS-CX switches. You want
to assign managers to groups on the AOS-CX switch by name.
How do you configure this setting in a CPPM TACACS+ enforcement profile?
A company uses both HPE Aruba Networking ClearPass Policy Manager (CPPM) and HPE Aruba Networking ClearPass Device Insight (CPDI).
What is one way integrating the two solutions can help the company implement Zero Trust Security?
A company wants to apply a standard configuration to all AOS-CX switch ports and have the ports dynamically adjust their configuration based on the identity of
the user or device that connects. They want to centralize configuration of the identity-based settings as much as possible.
What should you recommend?
What role can Internet Key Exchange (IKE)/IKEv2 play in an HPE Aruba Networking client-to-site VPN?
You are using OpenSSL to obtain a certificate signed by a Certification Authority (CA). You have entered this command:
openssl req -new -out file1.pem -newkey rsa:3072 -keyout file2.pem
Enter PEM pass phrase: **********
Verifying - Enter PEM pass phrase: **********
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:California
Locality Name (eg, city) []:Sunnyvale
Organization Name (eg, company) [Internet Widgits Pty Ltd]:example.com
Organizational Unit Name (eg, section) []:Infrastructure
Common Name (e.g. server FQDN or YOUR name) []:radius.example.com
What is one guideline for continuing to obtain a certificate?
You have created this rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) service's enforcement policy: IF Authorization [Endpoints Repository]
Conflict EQUALS true THEN apply "quarantine_profile"
What information can help you determine whether you need to configure cluster-wide profiler parameters to ignore some conflicts?
HPE Aruba Networking Central displays a Gateway Threat Count alert in the alert list. How can you gather more information about what caused the alert to trigger?
Refer to Exhibit:
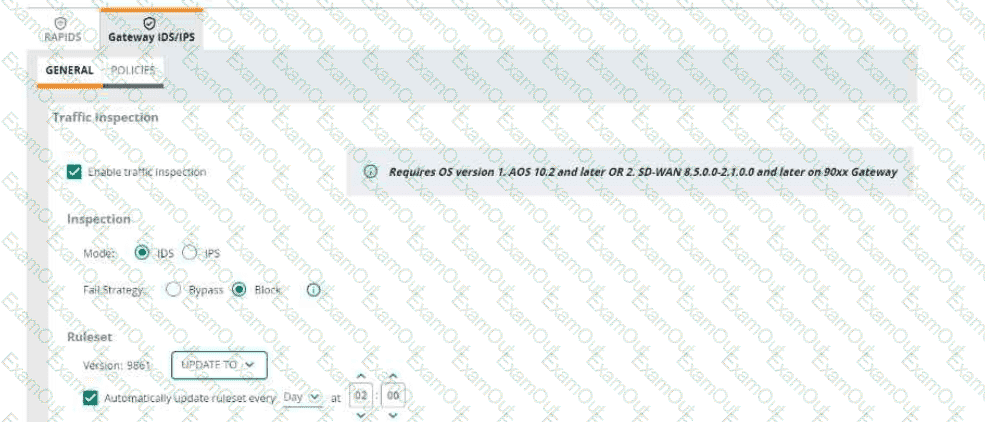
An HPE Aruba Networking 9x00 gateway is part of an HPE Aruba Networking Central group that has the settings shown in the exhibit. What would cause the gateway to drop traffic as part of its IDPS settings?
A company is using HPE Aruba Networking ClearPass Device Insight (CPDI) (the standalone application). In the CPDI security settings, Security Analysis is On, the Data Source is ClearPass Device Insight, and Enable Posture Assessment is On. You see that a device has a Risk Score of 90.
What can you know from this information?
A company has HPE Aruba Networking APs and AOS-CX switches, as well as HPE Aruba Networking ClearPass. The company wants CPPM to have HTTP User-
Agent strings to use in profiling devices.
What can you do to support these requirements?

