Which collectors can be used for device profiling? (Select two.)
Refer to the exhibit.
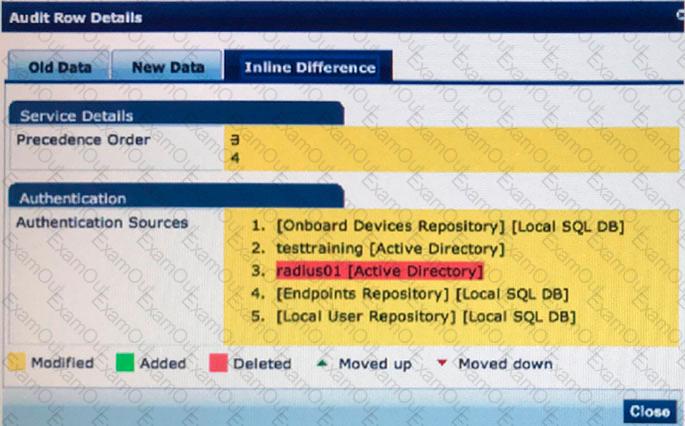
What information can be drawn from the audit row detail shown? (Select two.)
ClearPass and a wired switch are configured for 802.1x authentication with RADIUS CoA (RFC 3576) on UDP port 3799. This port has been blocked by a firewall between the wired switch and ClearPass.
What will be the outcome of this state?
Refer to the exhibit.
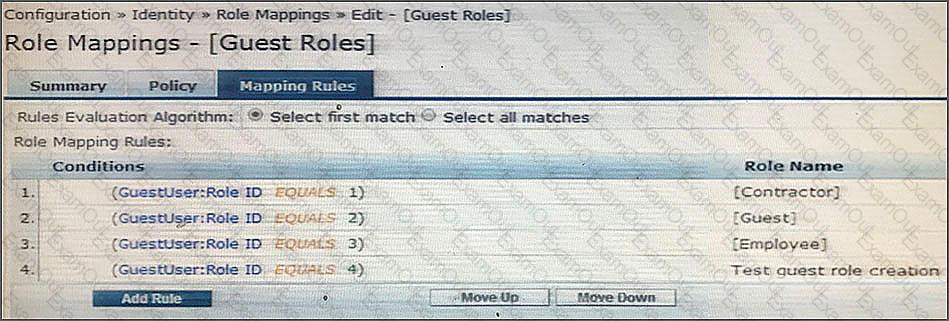
Based on the Guest Role Mapping Policy shown, what is the purpose of the Role Mapping Policy?
Which authentication protocols can be used for authenticating Windows clients that are Onboarded? (Select two.)
Which steps are required to use ClearPass as a TACACS+ Authentication server for a network device? (Select two.)
Which statement is true about the configuration of a generic LDAP server as an External Authentication server in ClearPass? (Choose three.)
A hotel chain deployed ClearPass Guest. When hotel guests connect to the Guest SSID, launch a web browser and enter the address www.google.com, they are unable to immediately see the web login page.
What are the likely causes of this? (Select two.)
Refer to the exhibit.

Based on the information shown, what is the purpose of using [Time Source] for authorization?
Refer to the exhibit.
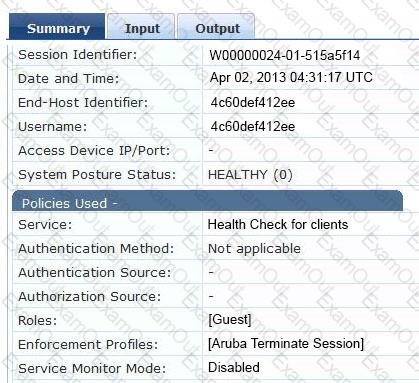
Based on the Access Tracker output for the user shown, which statement describes the status?

