You are migrating an application into the cloud The application will need to read data from a Cloud Storage bucket. Due to local regulatory requirements, you need to hold the key material used for encryption fully under your control and you require a valid rationale for accessing the key material.
What should you do?
You are part of a security team investigating a compromised service account key. You need to audit which new resources were created by the service account.
What should you do?
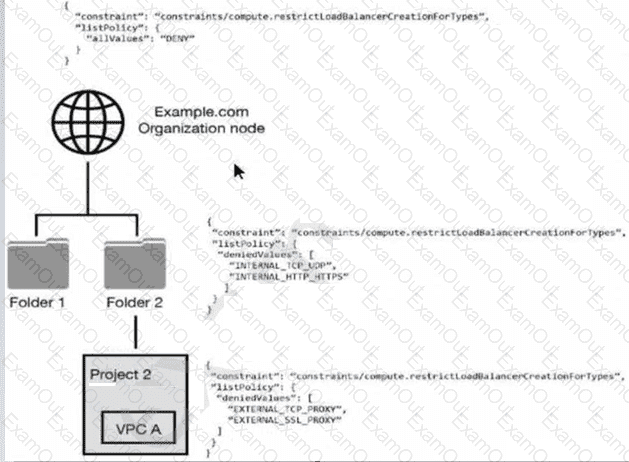
You have the following resource hierarchy. There is an organization policy at each node in the hierarchy as shown. Which load balancer types are denied in VPC A?
Your company is concerned about unauthorized parties gaming access to the Google Cloud environment by using a fake login page. You must implement a solution to protect against person-in-the-middle attacks.
Which security measure should you use?
You must ensure that the keys used for at-rest encryption of your data are compliant with your organization's security controls. One security control mandates that keys get rotated every 90 days. You must implement an effective detection strategy to validate if keys are rotated as required. What should you do?
You want to set up a secure, internal network within Google Cloud for database servers. The servers must not have any direct communication with the public internet. What should you do?
You are tasked with exporting and auditing security logs for login activity events for Google Cloud console and API calls that modify configurations to Google Cloud resources. Your export must meet the following requirements:
Export related logs for all projects in the Google Cloud organization.
Export logs in near real-time to an external SIEM.
What should you do? (Choose two.)
Your company is deploying a new application on GKE. The application handles sensitive customer data and is subject to strict data residency requirements. You need to ensure that the data is stored only within the europe-west4 region. What should you do?
A customer’s internal security team must manage its own encryption keys for encrypting data on Cloud Storage and decides to use customer-supplied encryption keys (CSEK).
How should the team complete this task?

