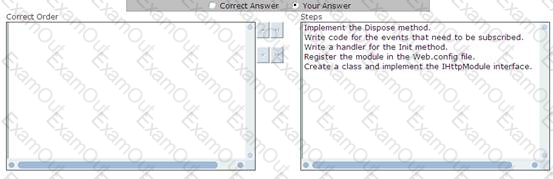
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You create an ASP.NET Web application using the .NET Framework 3.5. You want to use a HTTP module called on each and every request made by the application. It is called as part of the ASP.NET request pipeline. It has right to access life-cycle events throughout the request. You also want to ensure that the HTTP module allows a user to inspect incoming and outgoing requests and take appropriate action based on the request. What will be the correct order to create the HTTP module?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a method to call a COM component using the .NET Framework. You want to use declarative security to request the runtime to run a complete stack walk. You need to ensure that all callers be obliged to level of trust for COM interop before the callers execute the method. Which of the following attributes will you place on the method to accomplish the task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You have recently finished development of a Windows application using .NET Framework. Users report that the application is not running properly. When the users try to complete a particular action, the following error message comes out:
Unable to find assembly 'myservices, Version=1.0.0.0, Culture=neutral,
PublicKeyToken=29b5ad26c9de9b95'.
You notice that the error occurs as soon as the application tries to call functionality in a serviced component that was registered by using the following command:
regsvcs.exe myservices.dll
You must make sure that the application can call the functionality in the serviced component with no exceptions being thrown. What will you do to accomplish this task?
You work as a Web Administrator for BlueWell Inc. The company's sales employees access the Web server from remote locations via the Internet using Netscape Navigator or Internet Explorer. You want to secure the Web server. To secure the Web server, you want to use cookieless forms authentication. Which of the following properties will you use to accomplish the task?
Which of the following techniques is used to transmit passwords during authentication?
Which of the following modes can be used to configure the Remote Debugging Monitor for remote debugging?
You work as a Software Developer for ManSoft Inc. You use C# .NET to create an assembly named TestAssembly that will be used by other applications, including a standard COM client application. You must deploy the assembly on the COM application to a client computer. You must ensure that the COM applications can instantiate components within the assembly as COM components. Which of the following options will you use to accomplish this task?
You work as a Software Developer for ManSoft Inc. The company uses Visual Studio.NET 2005 as its application development platform. You have recently created an application that includes the code shown below.
string str1 = "ABC";
string str2 = "u";
str2 += "Certify";
Console.WriteLine(str1 == str2);
Console.WriteLine((Object) str1 == (Object) str2);
Console.WriteLine(str1.Equals(str2));
What will be the output of the above code?
You work as a Software Developer for ABC Inc. You create an ASP.NET Web application named MyWebApplication. You want to provide secure access to company's customers. You want to enable users to access the site from any browser by providing their user name and password. Which of the following authentication methods will you use to accomplish this task?
Henry works as a Software Developer for SoftTech Inc. He creates a Windows form named
MyForm1. The form contains detailed information about a student. The form uses a ListBox control named ListBox1 that concatenates two strings displayed in two TextBox controls. Henry wants a method to return a value for the control. Which of the following options will he consider while creating a method for the control?

