You work as a Software Developer for Blue Well Inc. You create a mobile Web application for
mobile users. You want to ensure that a cookieless session is implemented on it. Which of the
following statements are the main reasons of implementing a cookieless session on a mobile Web application?
Each correct answer represents a part of the solution. Choose two.
Tony works as a Software Developer for TechNet Inc. He creates a satellite assembly named
SatAssembly1. He wants to install SatAssembly1 in the global assembly cache. Therefore, he compiles the assembly by using the Al.exe tool and signs SatAssembly1. Which of the following possible tools will Tony use to sign SatAssembly1?
Each correct answer represents a complete solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create an ASP.NET Web application using .NET Framework 3.5. The application is hosted on Microsoft Windows Server 2008. Only FTP access is available to the server. You need to improve the searching of the pages in the search engines by taking action to URLs that do not have an .aspx file extension. You must ensure that all pages as well as static content can also be requested. What will you do to accomplish this?
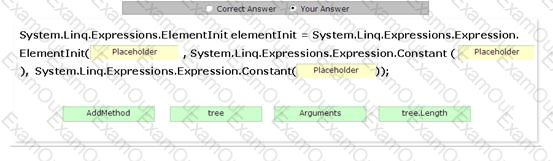
You work as an ADO.NET Application Developer for ABC Inc. The company uses Microsoft Visual Studio .NET 2008 as its application development platform. You create an ADO.NET application by using .NET Framework 3.5. You write the following code in the application:
string tree = "ABC";
System.Reflection.MethodInfo addMethod = typeof(Dictionary).GetMethod("Add");
You need to create an ElementInit that represents calling Dictionary.Add(tree.Length, tree). Drag and drop the appropriate values to accomplish the task.
You work as a Software Developer for ABC Inc. The company's server room is in a highly secured environment. The company wants to ensure that the server room uses thumb impressions for authentication. Which of the following authentication methods will you suggest?
You work as a Software Developer for ABC Inc. The company has several branches worldwide. The company uses Visual Studio .NET 2005 as its application development platform. You have received a file in ASCII encoded from one of the company's branch. Therefore, you are required to decode the file encoded in ACSII. Which of the following decoding types will you use to get the correct results?
Each correct answer represents a complete solution. Choose two.
Julia works as a Software Developer for Mansoft Inc. She develops an application using Visual Studio .NET. The application uses a method named MyMethod, which is located in an unmanaged DLL. Julia wants MyMethod to require the application to allocate unmanaged memory, fill the data, and pass the memory address to the application. She also wants to ensure that on returning from MyMethod, the application de-allocates the unmanaged memory. What will Julia do to accomplish the task?
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Windows application using .NET Framework 2.0. The application allows computer engineers to design circuit boards for different types of hardware. You create a custom control that represents the design surface. You are required to highlight the vacant areas on the design surface where a component can be dropped. Which of the following events will you use to accomplish this task?
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. You are using the StringBuilder class to string values. You want to create a StringBuilder object that can store 75 characters and should be initialized with "ABC". You also want to append a formatted string to the end of the StringBuilder object. Which of the following code segments will you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You are creating an ASP.NET Web application using .NET Framework 3.5. The application will be accessed by users from remote locations over the Internet. You need to use ASP.NET role management. You must ensure that any authorization information cached on remote client computers is as secure as possible. What will you do?

