John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using the Linux operating system. He wants to use a wireless sniffer to sniff the We-are-secure network. Which of the following tools will he use to accomplish his task?
You work as the Project Engineer for XYZ CORP. The company has a Unix-based network. Your office consists of one server, seventy client computers, and one print device. You raise a request for printing a confidential page. After 30 minutes, you find that your print request job is not processed and is at the seventh position in the printer queue. You analyze that it shall take another one hour to print. You decide to remove your job from the printer queue and get your page printed outside the office. Which of the following Unix commands can you use to remove your job from the printer queue?
John works as a Security Professional. He is assigned a project to test the security of www.we-are-secure.com. John wants to get the information of all network connections and listening ports in the numerical form. Which of the following commands will he use?
George works as an office assistant in Soft Well Inc. The company uses the Windows Vista operating system. He wants to disable a program running on a computer. Which of the following Windows Defender tools will he use to accomplish the task?
The Security Auditor's Research Assistant (SARA) is a third generation network security analysis tool. Which of the following statements are true about SARA? (Choose two)
Which of the following statements are true about the Enum tool?
Which of the following statements are true about a hot site?
Which of the following is a basic feature of the Unix operating system? (Choose three)
Which of the following types of servers are dedicated to provide resources to hosts on the network? (Choose three)
What will be the output of the following command? echo $(date %M) > date.txt

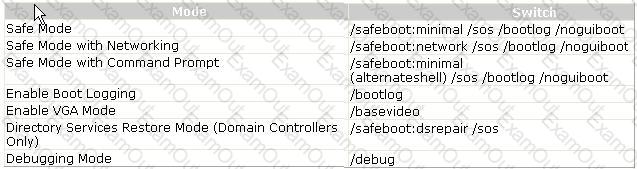 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG