You are the project manager of the NJJ project. Your enterprise environmental factors require that you establish certain risk management rules regarding low risks within your project. What is the best policy for risks with low probability and low impact in the project management?
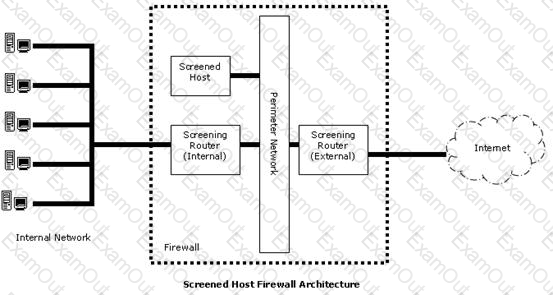
In the image of the Screened Host Firewall Architecture given below, select the element that is commonly known as the access router.
Which of the following tools can be used to read NetStumbler's collected data files and present street maps showing the logged WAPs as icons, whose color and shape indicates WEP mode and signal strength?
Which of the following types of attacks occurs when an attacker successfully inserts an intermediary software or program between two communicating hosts?
Adam works as a Penetration Tester for Umbrella Inc. He is assigned a project of testing the security of the company's network. He is using the Metasploit Framework for developing and executing exploit code against a remote target machine. The Metasploit Framework is the important sub-project of the Metasploit Project. Which of the following are the other sub-projects under the Metasploit projet?
Each correct answer represents a complete solution. Choose all that apply.
You work as the Network Administrator for a company that does a large amount of defense contract business. A high level of security, particularly regarding sensitive documents, is required. Which of the following are the steps you should take to secure network printers?
Each correct answer represents a complete solution. Choose two.
Which of the following statements about a certification authority (CA) is true?
You work as a Software Developer for PassGuide Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished the development of an application using .NET Framework 2.0. The application can be used only for cryptography. Therefore, you have implemented the application on a computer. What will you call the computer that implemented cryptography?
You are the project manager for the GHY Organization. A stakeholder has presented a change to your project that will cause the project scope to increase considerably. You are considering the change for approval and you need to review the impact of the change on all areas of the project. What change control system component is responsible for guiding the review of the impact of all changes on the project management knowledge areas?
Which of the following authentication methods is used to enable a Web browser to provide credentials when making a request during an HTTP transaction?
Which of the following is the process of comparing cryptographic hash functions of system executables and configuration files?
You are working in a functional organization and are managing the IHH Project. Your project will likely last for six months and has a budget constraint of $1,876,000. You'll be dealing with a functional manager to manage costs and resources in the project. Who will have authority over assigning the project team members to activities?
You are configuring IPS (Intrusion Prevention System) on a Cisco IOS router. The IPS Policy Wizard window opens when you confirm the SDEE messages. Which of the following tasks can you perform using the IPS Policy Wizard window?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following are outputs of the Direct and Manage Project Execution process?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following malware spread through the Internet and caused a large DoS attack in 1988?

