Which model is a software development process combining elements of both design and prototyping-in-stages, in an effort to combine advantages of top-down and bottom-up concepts?
You are a project manager for a recycling company. You are in the process of reviewing proposals from sellers for recycling equipment. You notice the scope statement states the company required to abide by the environmental agencies regulations regarding waste. As a result, you select proposals that automatically include features such as scrubbers and baghouses to reduce hazardous waste. Which of the following is true regarding the scope statement?
You are the Network Administrator for a large corporate network. You want to monitor all network traffic on your local network for suspicious activities and receive a notification when a possible attack is in process. Which of the following actions will you take for this?
Which of the following are the countermeasures against a man-in-the-middle attack?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Consumer Support Technician for ABC Inc. The company provides troubleshooting support to users. You are troubleshooting a computer of a user who is working on Windows Vista.
He reports that his sensitive data is being accessed by someone because of security vulnerability in the component of Windows Vista. Which of the following features of Windows Security Center will you configure to save the user's data?
Which of the following are the algorithms contained by the digital signature policy?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following features is used to generate spam on the Internet by spammers and worms?
Which of the following technologies is used to detect unauthorized attempts to access and manipulate computer systems locally or through the Internet or an intranet?
Which of the following is the process of rewriting source and destination addresses of IP packets as they pass through a router or firewall?
Which type of attack is the unauthorized access of information from a wireless device through a Bluetooth connection, often between phones, desktops, laptops, and PDAs?
US Garments wants all encrypted data communication between corporate office and remote location. They want to achieve following results:
• Authentication of users
• Anti-replay
• Anti-spoofing
• IP packet encryption
They implemented IPSec using Authentication Headers (AHs). Which results does this solution provide?
(Click the Exhibit button on the toolbar to see the case study.)
Each correct answer represents a complete solution. Choose all that apply.
Which of the following terms related to risk management represents the estimated frequency at which a threat is expected to occur?
The Incident handling process implemented in an enterprise is responsible to deal with all the incidents regarding the enterprise. Which of the following procedures will be involved by the preparation phase of the Incident handling process?
You are a project manager of a large construction project. Within the project you are working with several vendors to complete different phases of the construction. Your client has asked that you arrange for some of the materials a vendor is to install next week in the project to be changed. According to the change management plan what subsystem will need to manage this change request?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:
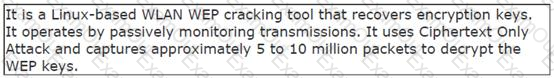
Which of the following tools is John using to crack the wireless encryption keys?

