Which of the following statements about policy is FALSE?
Which of the following statements about IPSec are true?
Each correct answer represents a complete solution. Choose two.
Your IT security team is responding to a denial of service attack against your server. They have taken measures to block offending IP addresses. Which type of threat control is this?
An application developer would like to replace Triple DES in their software with a stronger algorithm of the same type. Which of the following should they use?
Which field in the IPv6 header is used for QoS. or specifying the priority of the packet?
Which of the following statements best describes where a border router is normally placed?
Open the MATE terminal and use the tcpdump program to read - /pcaps /cass tech.pcap.
What is the source port number?
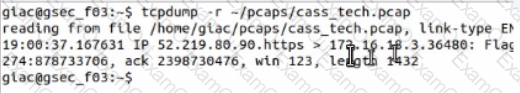
Where is the source address located in an IPv4 header?
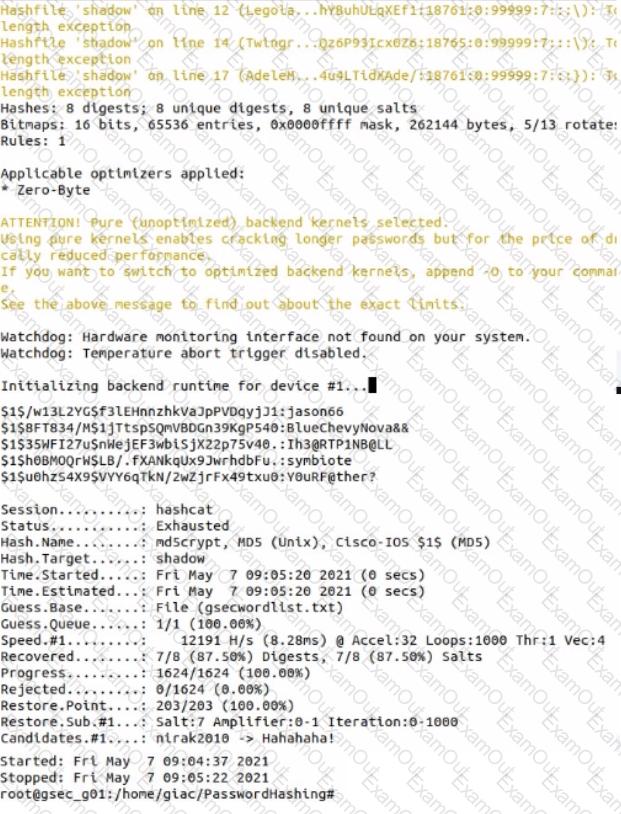
Use Hashcat to crack a local shadow file. What Is the password for the user account AGainsboro?
Hints
• The shadow file (shadow) and Hashcat wordlist (gsecwordlist.txt) are located in the directory /home /giac /PasswordHashing/
• Run Hashcat in straight mode (flag -a 0) to crack the MD5 hashes (flag -m 500) In the shadow file.
• Use the hash values from the Hashcat output file and the shadow file to match the cracked password with the user name.
• If required, a backup copy of the original files can be found in the shadowbackup directory.

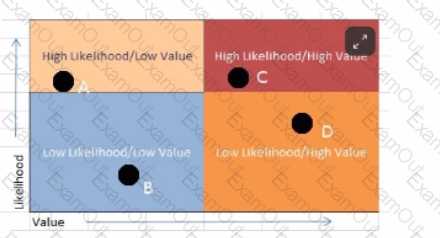
Analyze the screenshot below. In what order should the vulnerabilities be remediated?