In the AGULP model, who should be assigned permissions and privileges?
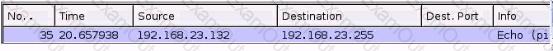
You are examining a packet capture session in Wire shark and see the packet shown in the accompanying image. Based on what you see, what is the appropriate protection against this type of attempted attack?
Why would someone use port 80 for deployment of unauthorized services?
In trace route results, what is the significance of an * result?
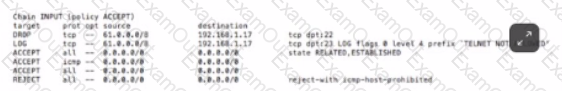
Based on the iptables output below, which type of endpoint security protection has host 192.168.1.17 implemented for incoming traffic on TCP port 22 (SSH) and TCP port 23 (telnet)?
Which of the following applications would be BEST implemented with UDP instead of TCP?
A web application requires multifactor authentication when a user accesses the application from a home office but does not require this when the user is in the office. What access control model is this describing?
What is TRUE about Workgroups and Domain Controllers?
Which of the following tools is used to configure, control, and query the TCP/IP network interface parameters?
Which common firewall feature can be utilized to generate a forensic trail of evidence and to identify attack trends against your network?

