Adam works as a professional Computer Hacking Forensic Investigator. He wants to investigate a suspicious email that is sent using a Microsoft Exchange server. Which of the following files will he review to accomplish the task?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following standards is used in wireless local area networks (WLANs)?
Which of the following United States laws protects stored electronic information?
You want to run the nmap command that includes the host specification of 202.176.56-57.*. How many hosts will you scan?
You have obtained the hash below from the /etc/shadow file. What are you able to discern simply by looking at this hash?
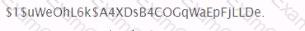
What difference would you expect to result from running the following commands;
(I). S dig ©ns domain.com target.com -t AXFR
and
(2). S dig ©ns.domain.com target.com -t IXFR=1002200301
John works as an Ethical Hacker for uCertify Inc. He wants to find out the ports that are open in uCertify's server using a port scanner. However, he does not want to establish a full TCP connection. Which of the following scanning techniques will he use to accomplish this task?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to perform a stealth scan to discover open ports and applications running on the We-are-secure server. For this purpose, he wants to initiate scanning with the IP address of any third party. Which of the following scanning techniques will John use to accomplish his task?
How many bits does SYSKEY use for encryption?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. In order to do so, he performs the following steps of the preattack phase successfully:
Information gathering
Determination of network range
Identification of active systems
Location of open ports and applications
Now, which of the following tasks should he perform next?

