Which of the following roles is used to ensure that the confidentiality, integrity, and availability of the services are maintained to the levels approved on the Service Level Agreement (SLA)?
Which of the following statements are true about classless routing protocols?
Each correct answer represents a complete solution. Choose two.
Shoulder surfing is a type of in-person attack in which the attacker gathers information about the premises of an organization. This attack is often performed by looking surreptitiously at the keyboard of an employee's computer while he is typing in his password at any access point such as a terminal/Web site. Which of the following is violated in a shoulder surfing attack?
The IT administrator wants to implement a stronger security policy. What are the four most important security priorities for uCertify Software Systems Pvt. Ltd.?
(Click the Exhibit button on the toolbar to see the case study.)
Firekiller 2000 is an example of a __________.
Which of the following processes is responsible for low risk, frequently occurring low cost changes?
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases.
The email header of the suspicious email is given below:
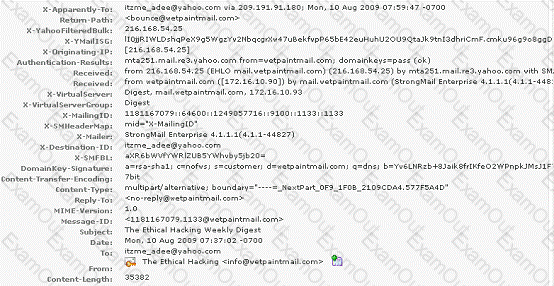
What is the IP address of the sender of this email?
Which of the following methods of encryption uses a single key to encrypt and decrypt data?
John works as a Network Security Professional. He is assigned a project to test the security of www.we-are-secure.com. He is working on the Linux operating system and wants to install an Intrusion Detection System on the We-are-secure server so that he can receive alerts about any hacking attempts. Which of the following tools can John use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following security applications is used to secure a database from unauthorized accesses in a network infrastructure?

