You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. You want to know the current TCP/IP network configuration settings, DHCP server IP address, and DHCP lease expiration date of your network.
Which of the following utilities will you use?
Which of the following is an asymmetric encryption algorithm?
Adam, a malicious hacker purposely sends fragmented ICMP packets to a remote target. The total size of this ICMP packet once reconstructed is over 65,536 bytes.
On the basis of above information, which of the following types of attack is Adam attempting to perform?
Which of the following commands will you use with the tcpdump command to capture the traffic from a filter stored in a file?
Which of the following is the default port for TACACS?
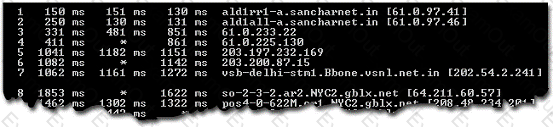
Which of the following utilities provides information as per the format given below?
Which of the following statements about Secure Shell (SSH) are true?
Each correct answer represents a complete solution. Choose three.
Which of the following statements about the traceroute utility are true?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Security Administrator for NetPerfect Inc. The company has a Windowsbased network. You are incharge of the data and network security of the company. While performing a threat log analysis, you observe that one of the database administrators is pilfering confidential data. What type of threat is this?
Adam, a novice Web user is getting large amount of unsolicited commercial emails on his email address. He suspects that the emails he is receiving are the Spam. Which of the following steps will he take to stop the Spam?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is a reason to implement security logging on a DNS server?
John works as a professional Ethical Hacker for SecureEnet Inc. The company has a Windowsbased network. All client computers run on Windows XP. A project has been assigned to John to investigate about the open ports responsible for various malicious attacks on the network. John wants to use the DOS command-line utility to find out the open ports. Which of the following DOS commands will John use to accomplish the task?
You work as a Network Administrator for McNeil Inc. The company has a TCP/IP-based network.
You are configuring an Internet connection for your company. Your Internet service provider (ISP) has a UNIX-based server. Which of the following utilities will enable you to access the UNIX server, using a text-based connection?
Which of the following protocols is used by voice over IP (VoIP) applications?
Which of the following terms describes an attempt to transfer DNS zone data?

