Which of the following proxy servers is also referred to as transparent proxies or forced proxies?
Which of the following is a chronological record of system activities to enable the reconstruction and examination of the sequence of events and/or changes in an event?
Which of the following tools performs comprehensive tests against web servers for multiple items, including over 6100 potentially dangerous files/CGIs?
Which of the following parts of IP header is used to specify the correct place of the fragment in the original un-fragmented datagram?
You work as a Security Administrator for Tech Perfect Inc. You have implemented and configured a web application security scanner in the company's network. It helps in the automated review of
the web applications with the defined purpose of discovering security vulnerabilities. In order to perform this task, the web application security scanner examines a number of vulnerabilities. What are these vulnerabilities?
Each correct answer represents a complete solution. Choose three.
Which of the following attacks sends false ICMP packets in an attempt to cripple a system using random fake Internet source addresses?
Which of the following IDs is used to reassemble the fragments of a datagram at the destination point?
Windump is a Windows port of the famous TCPDump packet sniffer available on a variety of platforms. In order to use this tool on the Windows platform a user must install a packet capture library.
What is the name of this library?
A scenario involves a pool of users with private IP addresses who need to access the Internet; however, the company has a limited number of IP addresses and needs to ensure users occupy only one public IP address.
Which technology is used to allow a pool of users to share one global IP address for Internet access?
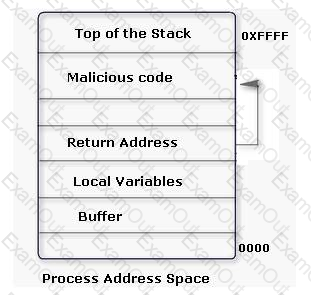
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
Which of the following tools can be used as a countermeasure to such an attack?