Which of the following refers to the process of adjusting the capacity of a company to meet the changed or predicted demands?
In which of the following categories can a computer security policy be categorized?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is used to govern the disclosure of financial and accounting information?
Which of the following are computer clusters that are implemented primarily for the purpose of providing high availability of services which the cluster provides?
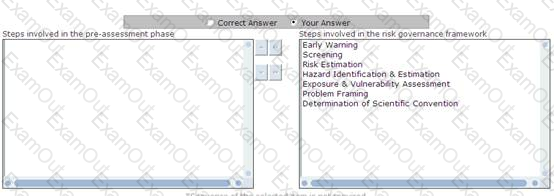
You work as a CRO for uCertify Inc. You and your team are involved in the pre-assessment phase of the risk governance framework. One of your newly joined team member wants to know the steps involved in the pre-assessment phase. Choose and reorder the steps performed in the pre-assessment phase.
Which of the following are the valid reasons for the occurrence of Drive-by download?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following should be considered while calculating the costs of the outage?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools can be used to detect steganography?
Rick works as a Computer Forensic Investigator for BlueWells Inc. He has been informed that some confidential information is being leaked out by an employee of the company. Rick suspects that someone is sending the information through email. He checks the emails sent by some employees to other networks. Rick finds out that Sam, an employee of the Sales department, is continuously sending text files that contain special symbols, graphics, and signs. Rick suspects that Sam is using the Steganography technique to send data in a disguised form. Which of the following techniques is Sam using?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following statements about incremental backup are true?
Each correct answer represents a complete solution. Choose two.

