Which of the following is a process of identifying and documenting project roles, responsibilities, and reporting relationships?
The disciplined and structured process, that integrates information security and risk management activities into the System Development Life Cycle, is provided by the risk management framework.
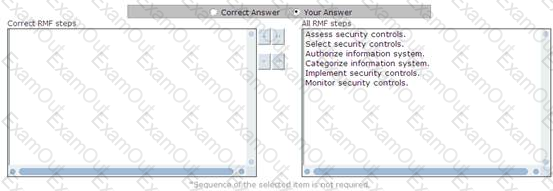
Choose the appropriate RMF steps.
You work as a Network Administrator for uCertify Inc. The organization has constructed a cafeteria for their employees and you are responsible to select the access control method for the cafeteria.
There are a few conditions for giving access to the employees, which are as follows:
1. Top level management can get access any time.
2. Staff members can get access during the specified hours.
3. Guests can get access only in working hours.
Which of the following access control methods is suitable to accomplish the task?
Which of the following states that a user should never be given more privileges than are required to carry out a task?
You work as a Security Administrator for uCertify Inc. You found that a person is coming inside the working area. Now, you want to ensure the authenticity of that person. By which of the following factors can you determine the accuracy of the authentication?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following procedures is to reduce the risk to personnel, property, and other assets while minimizing work disorders in the event of an emergency?
Single Loss Expectancy (SLE) represents an organization's loss from a single threat. Which of the following formulas best describes the Single Loss Expectancy (SLE)?
Which of the following sections come under the ISO/IEC 27002 standard?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following indicates that the project team has decided not to change the project management plan to deal with a risk?
You work as an Information Security Manager for uCertify Inc. You need to create the documentation on information security management system (ISMS). Which of the following is the governing principle behind ISMS?

