Which of the following is the correct formula of single loss expectancy?
Which of the following is used for secure financial transactions over the Internet?
Which of the following is expressly set up to attract and trap people who attempt to penetrate other people's computer systems?
You work as a Security Administrator for uCertify Inc. You need to make a documentation to provide ongoing education and awareness training of disciplinary actions of your company. What are the primary reasons to create this documentation?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following operations are performed by the Identity Management Process?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following should be considered while calculating the costs of the outage?
Each correct answer represents a complete solution. Choose all that apply.
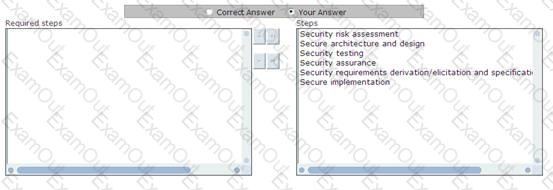
Cigital Risk Management Method was developed by Gary McGraw of Cigital and John Viega of Stonewall Software, and it defines software security risk management process. Choose and re-order the risk management steps that are included in this method.
You are working with a company that depends on real time data being available to employees, thus performance is an issue. They are trying to select the best method for handing the situation of a hard drive crashing. Which of the following would you recommend to them?
Which of the following are the uses of cryptography as defined in a policy document?
Each correct answer represents a complete solution. Choose all that apply.
You work as the Network Security Administrator for uCertify Inc. You are responsible for protecting your network from unauthorized access from both inside and outside the organization. For outside attacks, you have installed a number of security tools that protect your network. For internal security, employees are using passwords more than 8 characters; however, a few of them having the same designation often exchange their passwords, making it possible for others to access their accounts.
There is already a policy to stop this practice, but still employees are doing so. Now, you want to stop this and ensure that this never happens again. Which of the following will be the best step to stop this practice?

