Which of the following forms the basis for the assessment of information security management system (ISMS)?
David works as the Network Administrator for Blue Well Inc. One of his tasks is to develop and maintain risk management plan. Which of the following are the objectives of risk management plan?
Each correct answer represents a complete solution. Choose all that apply.
Sam works as a Project Manager for Blue Well Inc. He is working on a new project. He wants to access high level risks for the project. Which of the following steps should Sam take in order to accomplish the task?
David has identified a technical risk in his project and has been assigned a contingency for that. Which part of the risk response strategy does planning contingency reserves come under?
Which of the following pillars of Basel II is concerned with maintenance of regulatory capital intended for three major components of risk that a bank faces, which are credit risk, operational risk, and market risk?
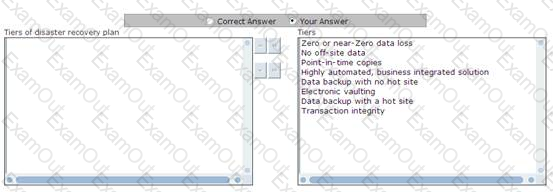
Disaster recovery plan consists of various tiers for identifying the methods of recovering mission-critical computer systems that are necessary to support business continuity. All these tiers provide a simple method to define current service levels and associated risks. Choose and re-order the tiers of disaster recovery plan.
Which of the following statements is true about annualized loss expectancy?
You work as an Information Security Manager for uCertify Inc. You are working on asset management. You need to differentiate various assets of your organization. Which of the following is an intangible asset?
Which of the following is a structured approach to transitioning individuals, teams, and organizations from a current state to a desired future state?
You work as an Information Security Manager for uCertify Inc. You need to make the documentation on change management. What are the advantages of using change management?
Each correct answer represents a complete solution. Choose all that apply.

