Eve stole a file named secret.txt, transferred it to her computer and she just entered these commands:
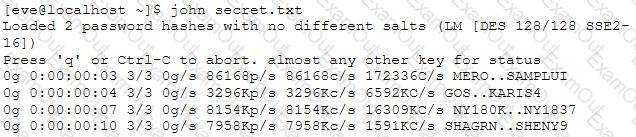
What is she trying to achieve?
Due to a slowdown of normal network operations, IT department decided to monitor internet traffic for all of the employees. From a legal stand point, what would be troublesome to take this kind of measure?
The "white box testing" methodology enforces what kind of restriction?
What two conditions must a digital signature meet?
Seth is starting a penetration test from inside the network. He hasn't been given any information about the network. What type of test is he conducting?
Which of the following is a low-tech way of gaining unauthorized access to systems?
On performing a risk assessment, you need to determine the potential impacts when some of the critical business process of the company interrupt its service. What is the name of the process by which you can determine those critical business?
Which is the first step followed by Vulnerability Scanners for scanning a network?
What would you enter, if you wanted to perform a stealth scan using Nmap?
Which of the following cryptography attack is an understatement for the extraction of cryptographic secrets (e.g. the password to an encrypted file) from a person by a coercion or torture?
Some clients of TPNQM SA were redirected to a malicious site when they tried to access the TPNQM main site. Bob, a system administrator at TPNQM SA, found that they were victims of DNS Cache Poisoning.
What should Bob recommend to deal with such a threat?
If an attacker uses the command SELECT*FROM user WHERE name = ‘x’ AND userid IS NULL; --‘; which type of SQL injection attack is the attacker performing?
Analyst is investigating proxy logs and found out that one of the internal user visited website storing suspicious Java scripts. After opening one of them, he noticed that it is very hard to understand the code and that all codes differ from the typical Java script. What is the name of this technique to hide the code and extend analysis time?
In the field of cryptanalysis, what is meant by a “rubber-hose" attack?
Chandler works as a pen-tester in an IT-firm in New York. As a part of detecting viruses in the systems, he uses a detection method where the anti-virus executes the malicious codes on a virtual machine to simulate CPU and memory activities.
Which type of virus detection method did Chandler use in this context?

