What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a _____ database structure instead of SQL’s _____ structure. Because of this, LDAP has difficulty representing many-to-one relationships.
Study the snort rule given below:
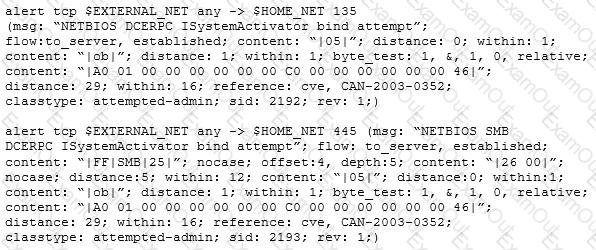
From the options below, choose the exploit against which this rule applies.
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.
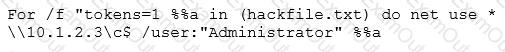
What is Eve trying to do?
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
What is the purpose of DNS AAAA record?
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that allows session oriented connections (Telnet) and performs the sequence prediction on the target operating system. He manages to find an active session due to the high level of traffic on the network. What is Bob supposed to do next?
What is GINA?
You are analysing traffic on the network with Wireshark. You want to routinely run a cron job which will run the capture against a specific set of IPs - 192.168.8.0/24. What command you would use?
Password cracking programs reverse the hashing process to recover passwords. (True/False.)
Take a look at the following attack on a Web Server using obstructed URL:
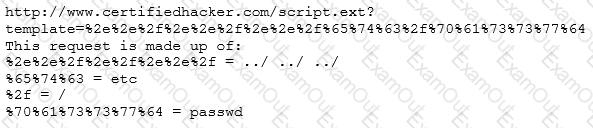
How would you protect from these attacks?
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
A network security administrator is worried about potential man-in-the-middle attacks when users access a corporate web site from their workstations. Which of the following is the best remediation against this type of attack?
A certified ethical hacker (CEH) completed a penetration test of the main headquarters of a company almost two months ago, but has yet to get paid. The customer is suffering from financial problems, and the CEH is worried that the company will go out of business and end up not paying. What actions should the CEH take?
Which of the following is optimized for confidential communications, such as bidirectional voice and video?

