An ethical hacker for a large security research firm performs penetration tests, vulnerability tests, and risk assessments. A friend recently started a company and asks the hacker to perform a penetration test and vulnerability assessment of the new company as a favor. What should the hacker's next step be before starting work on this job?
Which of the following network attacks takes advantage of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
Which of the following cryptography attack methods is usually performed without the use of a computer?
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
In the OSI model, where does PPTP encryption take place?
What is the best defense against privilege escalation vulnerability?
Which protocol and port number might be needed in order to send log messages to a log analysis tool that resides behind a firewall?
Which of the following is a client-server tool utilized to evade firewall inspection?
What are the three types of compliance that the Open Source Security Testing Methodology Manual (OSSTMM) recognizes?
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:
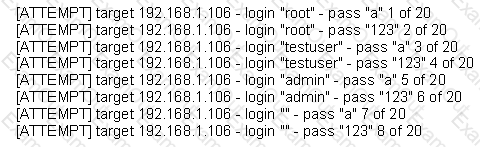
What is most likely taking place?
Which of the following is a preventive control?
Which of the following is used to indicate a single-line comment in structured query language (SQL)?
What is the main advantage that a network-based IDS/IPS system has over a host-based solution?
A Network Administrator was recently promoted to Chief Security Officer at a local university. One of employee's new responsibilities is to manage the implementation of an RFID card access system to a new server room on campus. The server room will house student enrollment information that is securely backed up to an off-site location.
During a meeting with an outside consultant, the Chief Security Officer explains that he is concerned that the existing security controls have not been designed properly. Currently, the Network Administrator is responsible for approving and issuing RFID card access to the server room, as well as reviewing the electronic access logs on a weekly basis.
Which of the following is an issue with the situation?
A company has hired a security administrator to maintain and administer Linux and Windows-based systems. Written in the nightly report file is the followinG.
Firewall log files are at the expected value of 4 MB. The current time is 12am. Exactly two hours later the size has decreased considerably. Another hour goes by and the log files have shrunk in size again.
Which of the following actions should the security administrator take?
What are the three types of authentication?
How can a policy help improve an employee's security awareness?
While checking the settings on the internet browser, a technician finds that the proxy server settings have been checked and a computer is trying to use itself as a proxy server. What specific octet within the subnet does the technician see?
A hacker is attempting to see which IP addresses are currently active on a network. Which NMAP switch would the hacker use?
The SYN flood attack sends TCP connections requests faster than a machine can process them.
Attacker creates a random source address for each packet
SYN flag set in each packet is a request to open a new connection to the server from the spoofed IP address
Victim responds to spoofed IP address, then waits for confirmation that never arrives (timeout wait is about 3 minutes)
Victim's connection table fills up waiting for replies and ignores new connections
Legitimate users are ignored and will not be able to access the server
How do you protect your network against SYN Flood attacks?

