A tunnel mode wireless network is configured on a FortiGate wireless controller.
Which task must be completed before the wireless network can be used?
Which of the following is a requirement to generate analytic reports using on-site FortiPresence deployment?
When using FortiPresence as a captive portal, which two types of public authentication services can be used to access guest Wi-Fi? (Choose two.)
Which two statements about distributed automatic radio resource provisioning (DARRP) are correct? (Choose two.)
Refer to the exhibit.
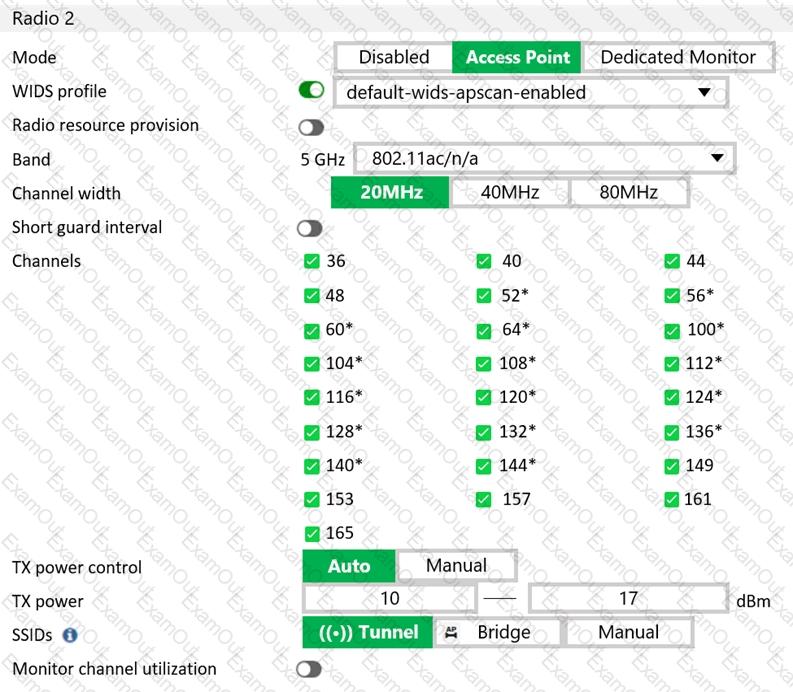
What does the asterisk (*) symbol beside the channel mean?
Which statement is correct about security profiles on FortiAP devices?
You are investigating a wireless performance issue and you are trying to audit the neighboring APs in the PF environment. You review the Rogue APs widget on the GUI but it is empty, despite the known presence of other APs.
Which configuration change will allow neighboring APs to be successfully detected?
How are wireless clients assigned to a dynamic VLAN configured for hash mode?
Six APs are located in a remotely based branch office and are managed by a centrally hosted FortiGate. Multiple wireless users frequently connect and roam between the APs in the remote office.
The network they connect to, is secured with WPA2-PSK. As currently configured, the WAN connection between the branch office and the centrally hosted FortiGate is unreliable.
Which configuration would enable the most reliable wireless connectivity for the remote clients?
Which two roles does FortiPresence analytics assist in generating presence reports? (Choose two.)

