A FortiMail device is configured with the protected domain example.com.
If none of the senders is authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
Refer to the exhibits showing SMTP limits (Session Profile — SMTP Limits), and domain settings (Domain Settings, and Domain Settings — Other) of a FortiMail device.
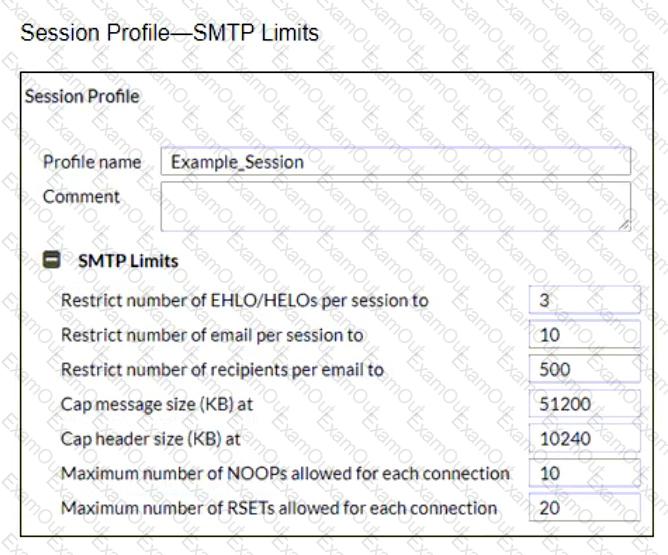
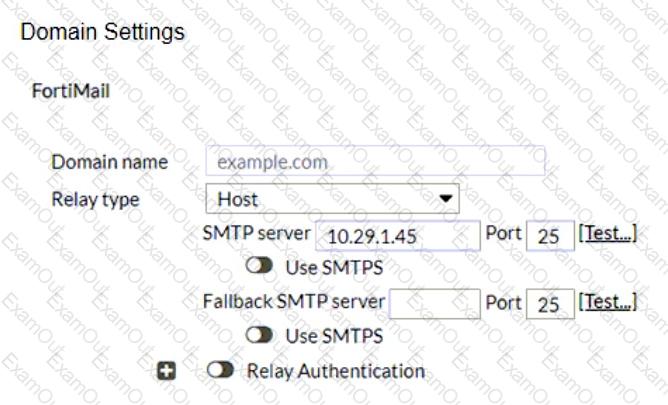
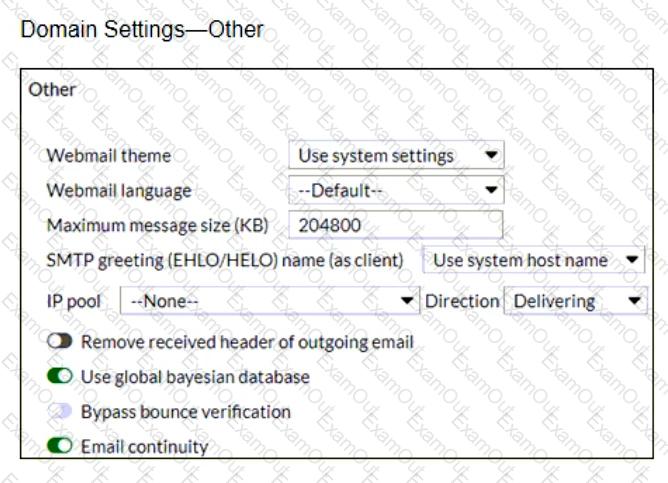
Which message size limit in KB will the FortiMail apply to outbound email?
Refer to the exhibit which shows the Authentication Reputation list on a gateway mode FortiMail device.
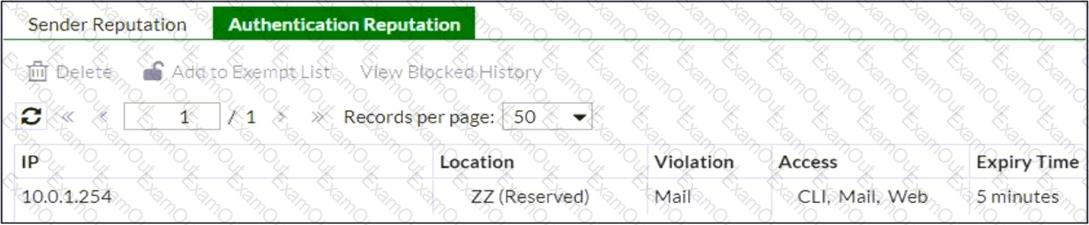
Why was the IP address blocked?
Refer to the exhibit which shows a topology diagram of a FortiMail cluster deployment.
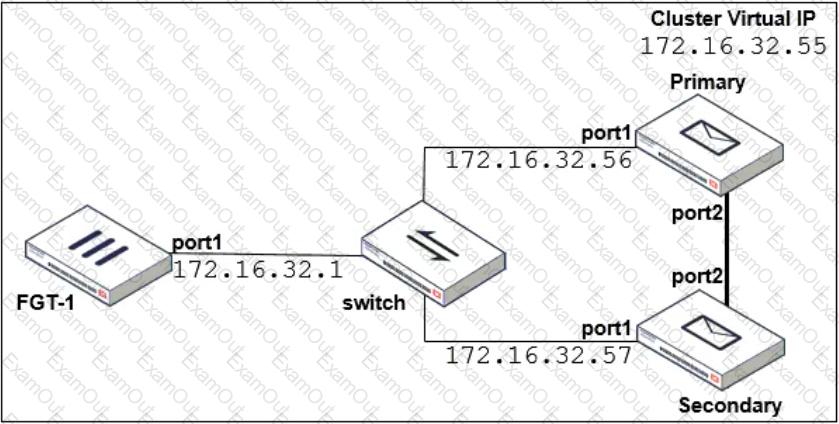
Which IP address must the DNS MX record for this organization resolve to?
Refer to the exhibit, which shows an inbound recipient policy.
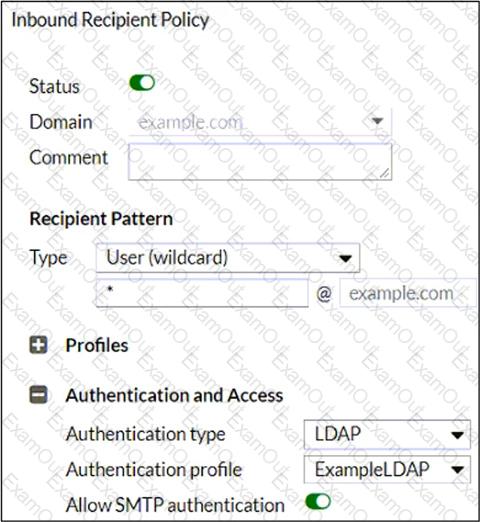
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9:INTERNAL.
Which two statements describe what this policy ID means? (Choose two.)
Refer to the exhibit, which shows a few lines of FortiMail logs.
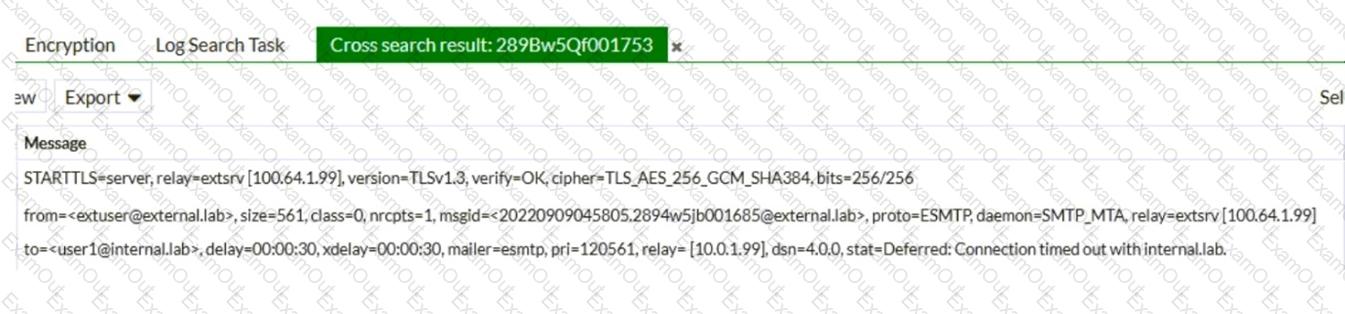
Based on these log entries, which two statements correctly describe the operational status of this FortiMail device? (Choose two.)
Refer to the exhibit which displays a history log entry.
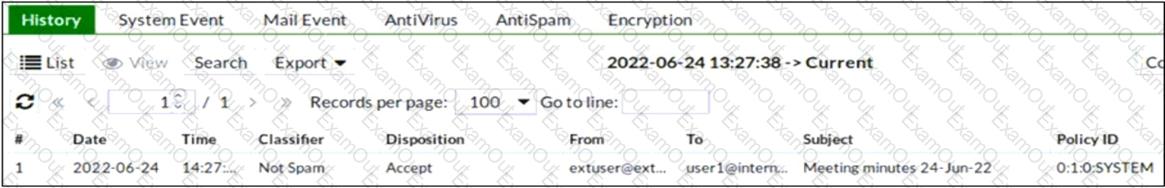
Why does the last field show SYSTEM in the Policy ID column?
An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas.
Which FortiMail feature specific to server mode can be used to accomplish this?

