You have configured the performance SLA with the probe mode as Prefer Passive.
What are two observable impacts of this configuration? (Choose two.)
Which two statements correctly describe what happens when traffic matches the implicit SD-WAN rule? (Choose two answers)
How does the FortiSASE security dashboard facilitate vulnerability management for FortiClient endpoints? (Choose one answer)
Refer to the exhibit.

The exhibit shows output of the command diagnose sys sdwan service collected on a FortiGate device.
The administrator wants to know through which interface FortiGate will steer traffic from local users on subnet 10.0.1.0/255.255.255.192 and with a destination of the social media application Facebook.
Based on the exhibits, which two statements are correct? (Choose two.)
Refer to the exhibits.
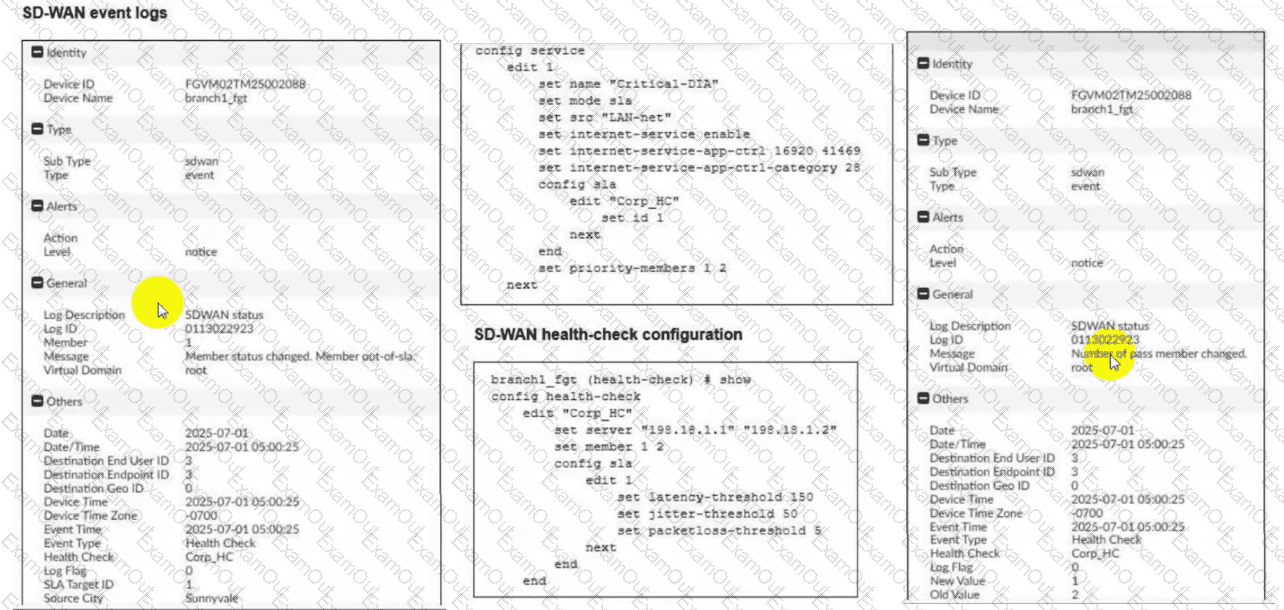
Two SD-WAN event logs, the member status, the SD-WAN rule configuration, and the health-check configuration for a FortiGate device are shown. Immediately after the log messages are displayed, how will the FortiGate steer the traffic based on the information shown in the exhibits? (Choose one answer)
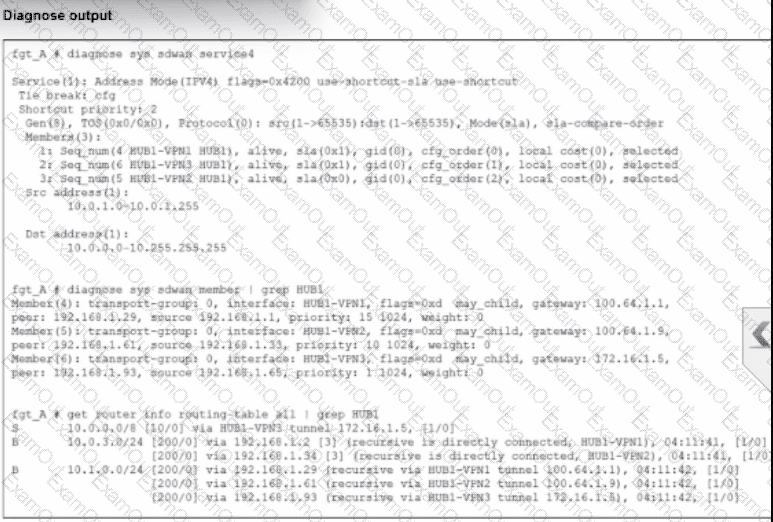
An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network. The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over HUB1-VPN1. However, the traffic is routed over HUB1-VPN3.
Based on the output shown in the exhibit, which two reasons, individually or together, could explain the observed behavior? (Choose two.)
SD-WAN interacts with many other FortiGate features. Some of them are required to allow SD-WAN to steer the traffic.
Which three configuration elements must you configure before FortiGate can steer traffic according to SD-WAN rules? (Choose three.)
An existing Fortinet SD-WAN customer who has recently deployed FortiSASE wants to have a comprehensive view of, and combined reports for, both SD-WAN branches and remote users. How can the customer achieve this?
Which two statements about configuring a steering bypass destination in FortiSASE are correct? (Choose two.)
Which statement about security posture tags in FortiSASE is correct?

