Refer to the exhibit.
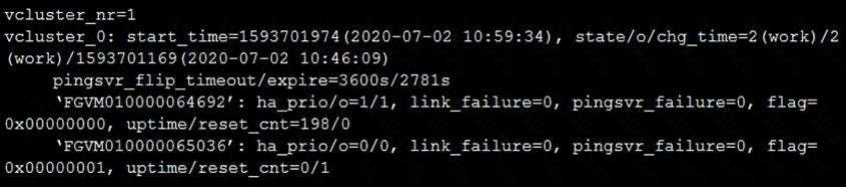
The exhibit displays the output of the CLI command: diagnose sys ha dump-by vcluster.
Which two statements are true? (Choose two.)
46
Which two types of traffic are managed only by the management VDOM? (Choose two.)
7
An administrator has a requirement to keep an application session from timing out on port 80. What two changes can the administrator make to resolve the issue without affecting any existing services running through FortiGate? (Choose two.)
Refer to the exhibit.
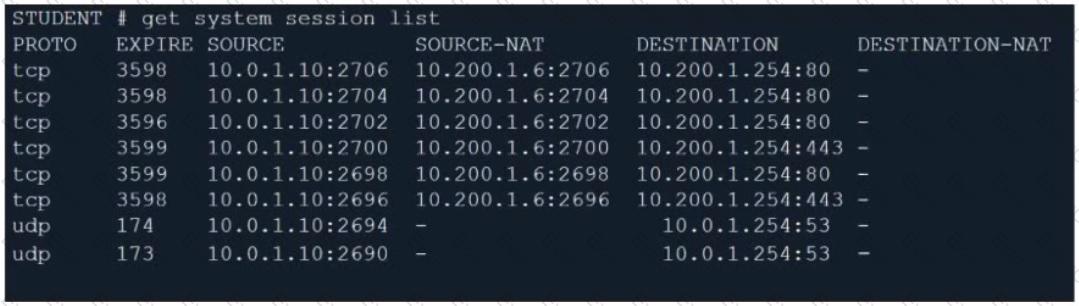
Which contains a session list output. Based on the information shown in the exhibit, which statement is true?
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
* All traffic must be routed through the primary tunnel when both tunnels are up
* The secondary tunnel must be used only if the primary tunnel goes down
* In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover
Which two key configuration changes are needed on FortiGate to meet the design requirements? (Choose two,)
The IPS engine is used by which three security features? (Choose three.)
Refer to the exhibit.
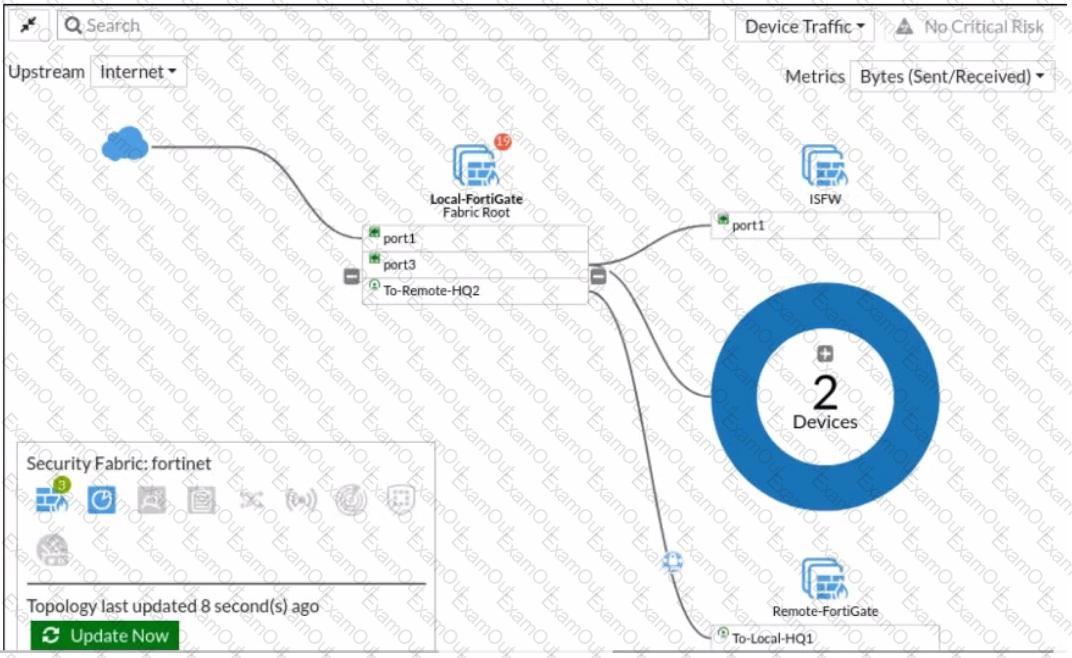
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)
Refer to the exhibit.
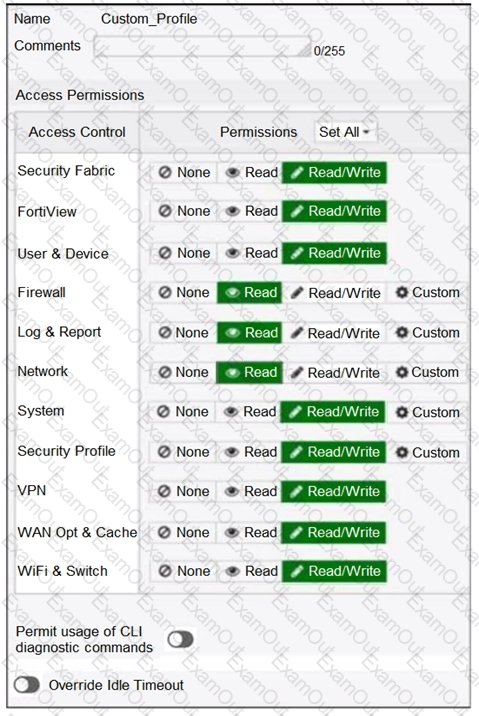
Based on the administrator profile settings, what permissions must the administrator set to run the diagnose firewall auth list CLI command on FortiGate?
Which two statements explain antivirus scanning modes? (Choose two.)
An administrator does not want to report the logon events of service accounts to FortiGate. What setting on the collector agent is required to achieve this?

