An administrator wants to configure Dead Peer Detection (DPD) on IPSEC VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when no traffic is observed in the tunnel.
Which DPD mode on FortiGate will meet the above requirement?
You have enabled logging on a FortiGate device for event logs and all security logs, and you have set up logging to use the FortiGate local disk.
What is the default behavior when the local disk is full?
73
If Internet Service is already selected as Source in a firewall policy, which other configuration objects can be added to the Source filed of a firewall policy?
Refer to the exhibit showing a debug flow output.
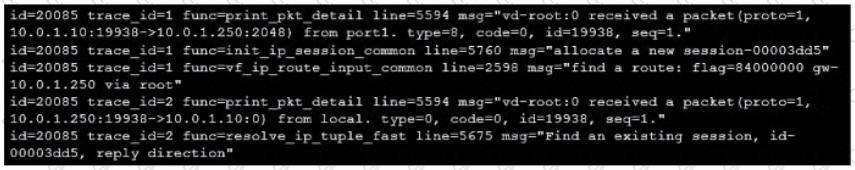
Which two statements about the debug flow output are correct? (Choose two.)
99
An administrator needs to configure VPN user access for multiple sites using the same soft FortiToken. Each site has a FortiGate VPN gateway. What must an administrator do to achieve this objective?
In an explicit proxy setup, where is the authentication method and database configured?
53
Which of the following conditions must be met in order for a web browser to trust a web server certificate signed by a third-party CA?
113
What inspection mode does FortiGate use if it is configured as a policy-based next-generation firewall (NGFW)?
27
Which feature in the Security Fabric takes one or more actions based on event triggers?
108
Which statement about the IP authentication header (AH) used by IPsec is true?

