Refer to the exhibits.
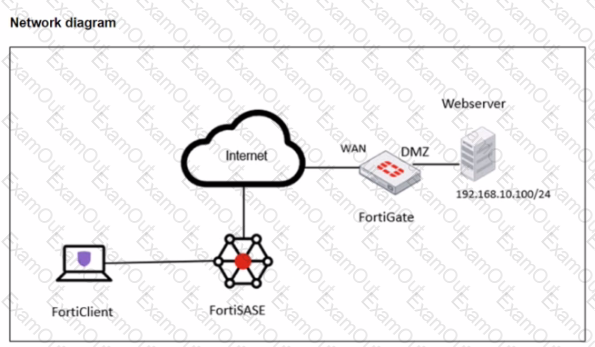
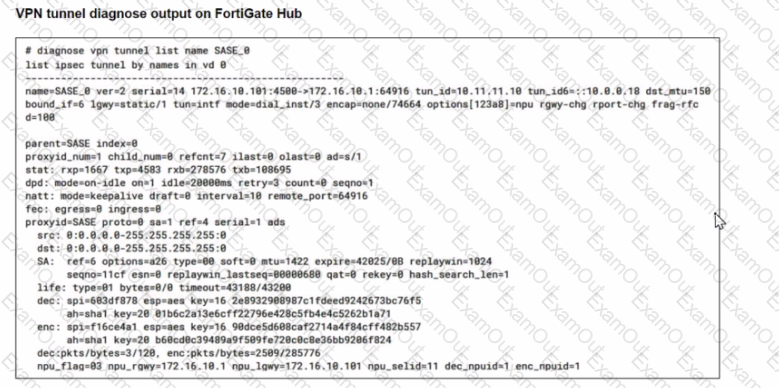
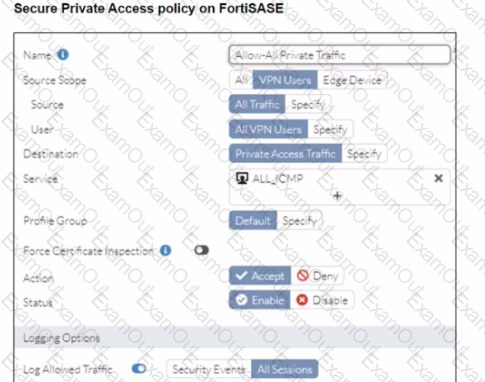
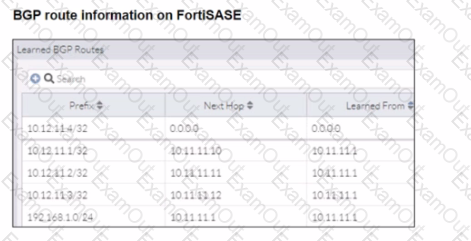

A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGale hub. However, the administrator is not able to ping the webserver hosted behind the FortiGate hub.
Based on the output, what is the reason for the ping failures?
Refer to the exhibit.
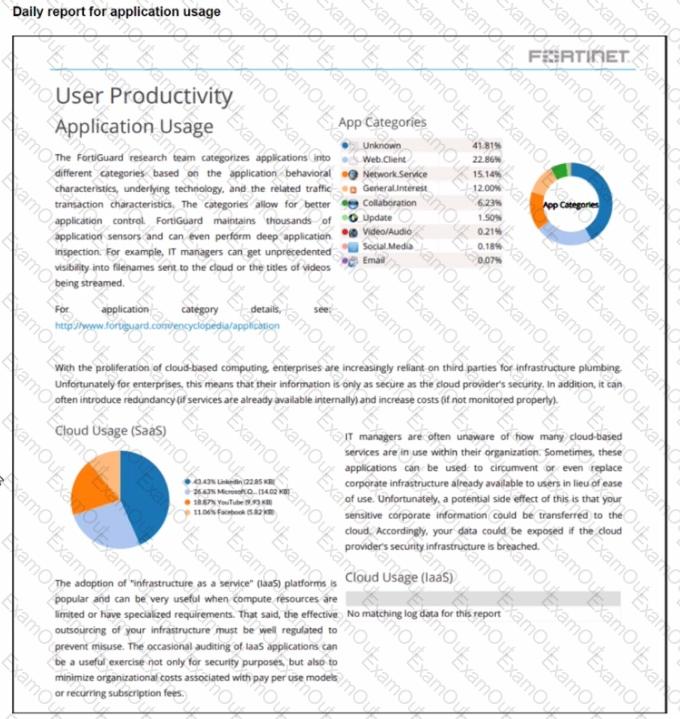
The daily report for application usage shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
What are two advantages of using zero-trust tags? (Choose two.)
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
When viewing the daily summary report generated by FortiSASE. the administrator notices that the report contains very little data. What is a possible explanation for this almost empty report?
Which two additional components does FortiSASE use for application control to act as an inline-CASB? (Choose two.)
Refer to the exhibit.
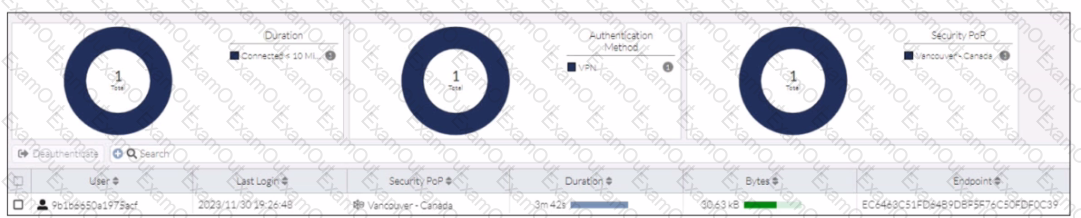
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters. Which configuration change must the administrator make to get proper user information?
A customer wants to upgrade their legacy on-premises proxy to a could-based proxy for a hybrid network. Which FortiSASE features would help the customer to achieve this outcome?
Which two deployment methods are used to connect a FortiExtender as a FortiSASE LAN extension? (Choose two.)

