An administrator notices multiple IP addresses attempting to log in to an application frequently, within a short time period. They suspect attackers are attempting to guess user passwords for a secure application.
What is the best way to limit this type of attack on FortiWeb, while still allowing legitimate traffic through?
Which implementation is most suited for a deployment that must meet PCI DSS compliance criteria?
Refer to the exhibit.
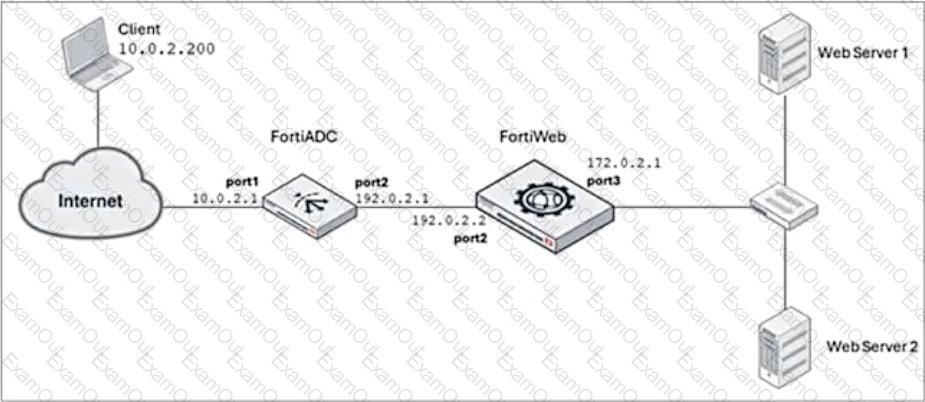
FortiADC is applying SNAT to all inbound traffic going to the servers.
When an attack occurs, FortiWeb blocks traffic based on the192.0.2.1source IP address, which belongs to FortiADC. This setup is breaking all connectivity and genuine clients are not able to access the servers.
What can the administrator do to avoid this problem? (Choose two.)
In which two operating modes can FortiWeb modify HTTP packets? (Choose two.)
Which is an example of a cross-site scripting (XSS) attack?
What are two results of enabling monitor mode on FortiWeb? (Choose two.)
A customer wants to be able to index your websites for search and advertisement purposes.
What is the easiest way to allow this on a FortiWeb?
An attacker attempts to send an SQL injection attack containing the known attack string 'root'; -- through an API call.
Which FortiWeb inspection feature will be able to detect this attack the quickest?
Refer to the exhibit.
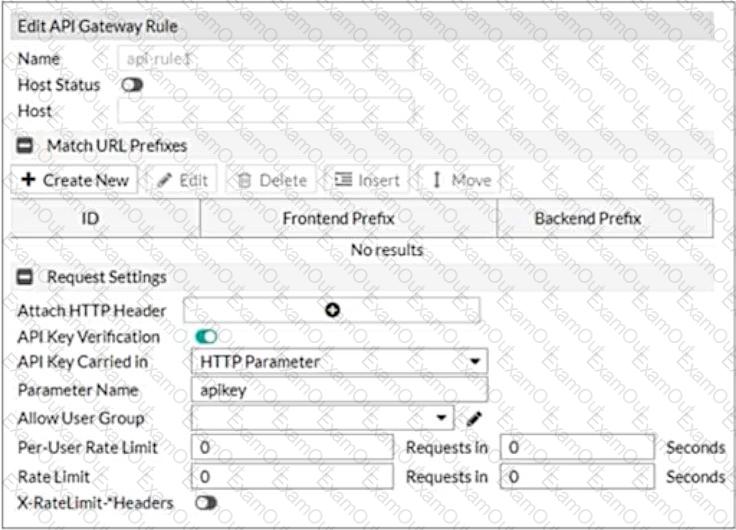
What are two additional configuration elements that you must be configure for this API gateway? (Choose two.)
Which command will enable debugging for the FortiWeb user tracking feature?


