You have recently grouped multiple FortiGate devices into a single ADOM. System Settings > Storage Info
shows the quota used.
What does the disk quota refer to?
An administrator has configured the following settings:
config system global
set log-checksum md5-auth
end
What is the significance of executing this command?
What is the purpose of the FortiAnalyzer command execute format disk?
Which statement about sending notifications with incident updates is true?
In order for FortiAnalyzer to collect logs from a FortiGate device, what configuration is required? (Choose two.)
Refer to the exhibit.
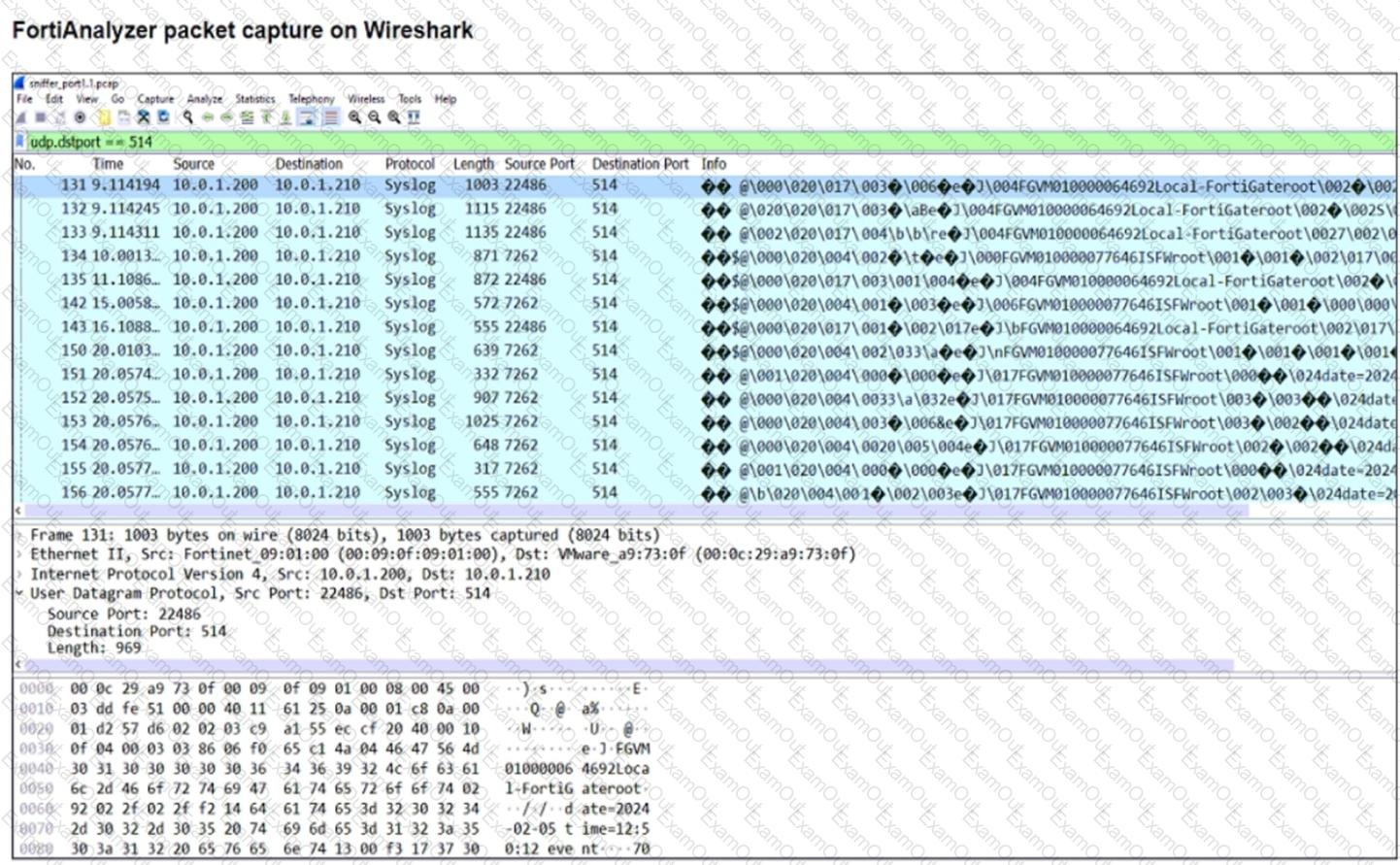
The capture displayed was taken on a FortiAnalyzer.
Why is a single IP address shown as the source for all logs received?
Refer to the exhibit.
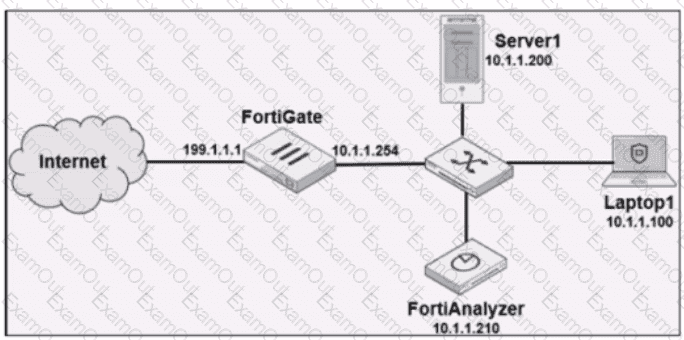
Laptop1 is used by several administrators to manage FortiAnalyzer. You want to configure a generic text filter that matches all login attempts to the web interface generated by any user other than "admin", and coming from Laptop1.
Which filter will achieve the desired result?
Refer to the exhibit.
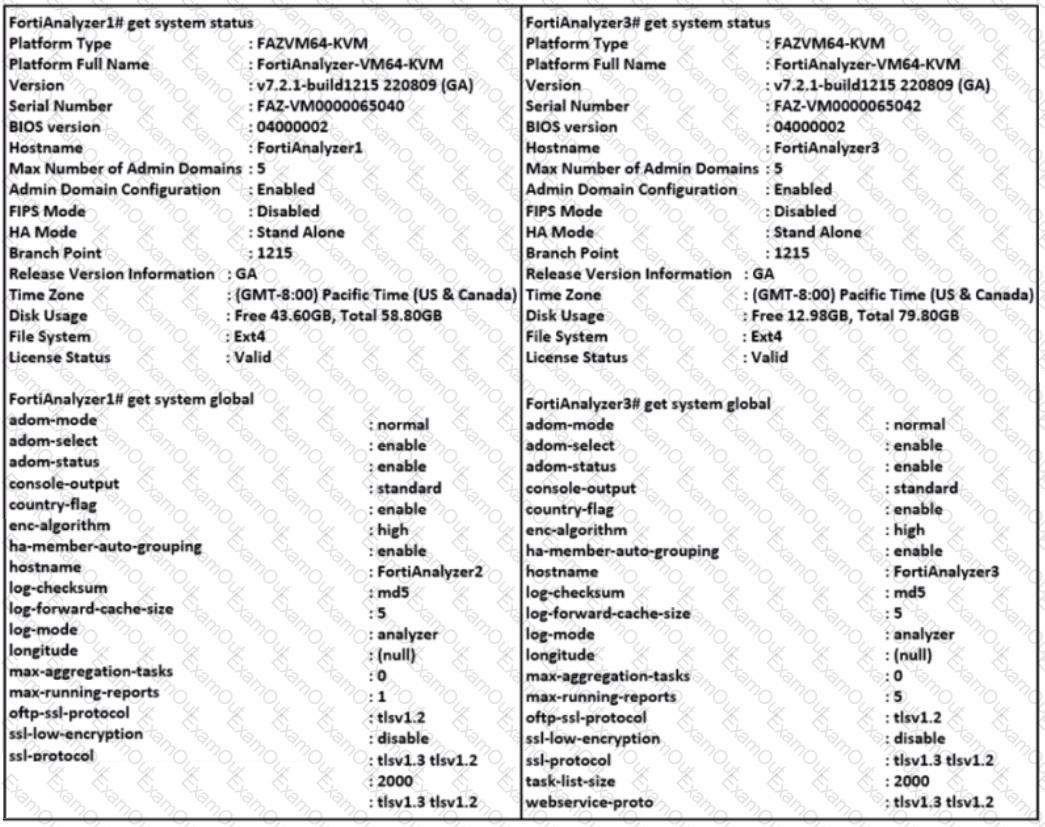
Based on the partial outputs displayed, which devices can be members of a FortiAnalyzer Fabric?
Which process is responsible for enforcing the log file size?
How can you attach a report to an incident?

