A BIG-IP Administrator wants to send packets from one subnet to another. What device is required to allow this to function?
A VoIP application requires that data payloads will NOT be fragmented. Which protocol controls network behavior in this situation?
Web application http://www.example.com at 10.10.1.1.110, is unresponsive. A recent change migrated DNS to a new platform
How does file caching affect the web application?
A BIG IP administrator is testing a web server behind ADC. The connection to a Virtual Server is successful but the page is still not loading Where should the administrator test to determine if theserver is available?
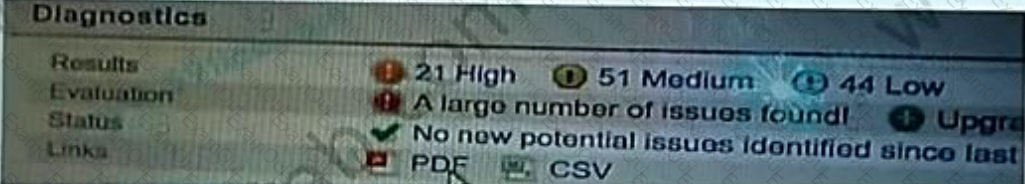
What is the correct procedure to comply with the recommendation?
In which FTP mode is the serve, responsible for initiating the data correction back to the client?
Exhibit.

the Web application Server made a query to the Database to present dynamic content for a user who would be the client?
Which security mode. functions by defining what traffic is allowed and rejecting all other traffic?
A new virtual server is being tested to replace http://myapp.mydomain.com. The original virtual server is still on use. And the new virtual server is on a different ip address. What should be done to test this new virtual server using the fully quailed domain name for this application?

