What is used to update information in a configuration management database?
What is the goal of lean practices in a software development methodology?
What describes network-attached storage (NAS)?
What term refers to businesses that do not have a digital plan, and have limited initiatives or investments related to digital transformation?
A consumer is interested in a service that provides multiple operating systems and programming frameworks for application development and deployment.
Which cloud service model meets these requirements?
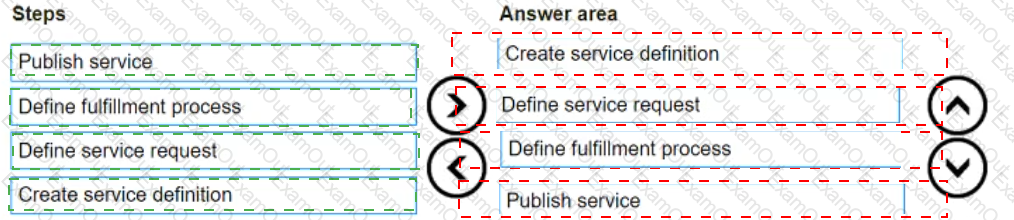
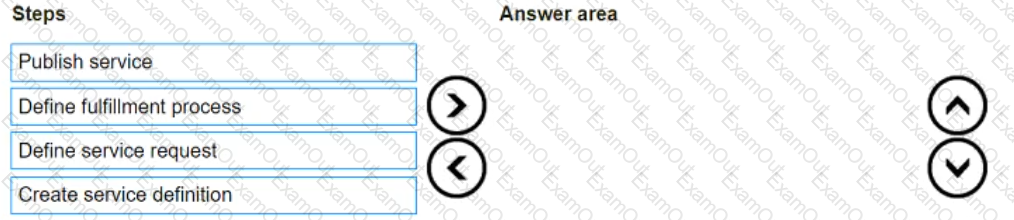
What is the correct sequence of steps in the service catalog design and implementation process?
What is the correct order of the business continuity plan principles?
What is true about change management?
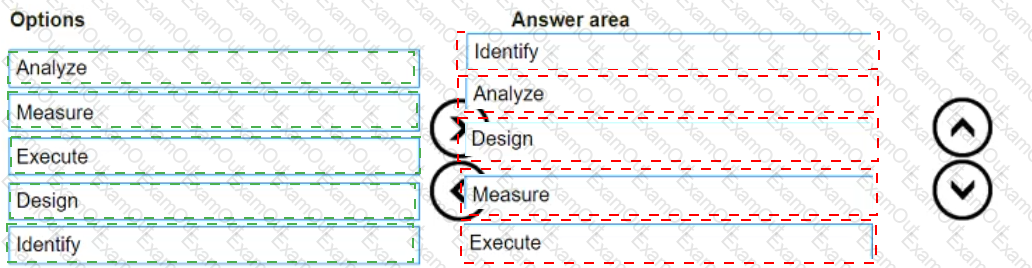
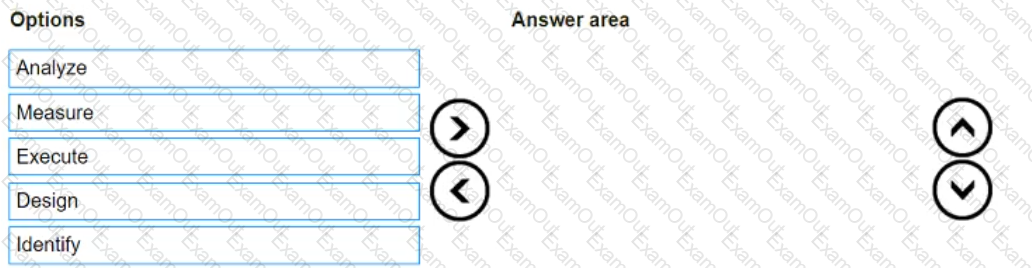
Which risk management process is in the correct order
Which host-based security attribute supports audit, multifactor authentication, and IP address filtering?