A security administrator notices that the log file of the company`s webserver contains suspicious entries:
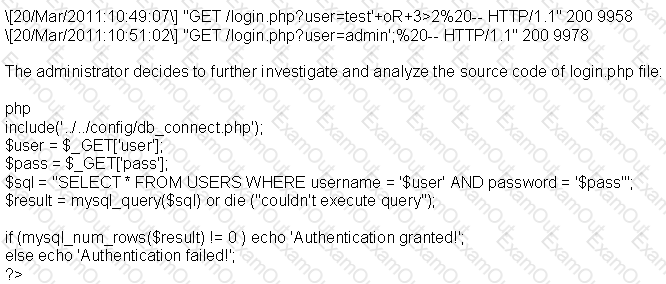
Based on source code analysis, the analyst concludes that the login.php script is vulnerable to
What is the outcome of the comm”nc -l -p 2222 | nc 10.1.0.43 1234"?
How can a rootkit bypass Windows 7 operating system’s kernel mode, code signing policy?
Which Open Web Application Security Project (OWASP) implements a web application full of known vulnerabilities?
A security consultant is trying to bid on a large contract that involves penetration testing and reporting. The company accepting bids wants proof of work so the consultant prints out several audits that have been performed. Which of the following is likely to occur as a result?
To send a PGP encrypted message, which piece of information from the recipient must the sender have before encrypting the message?
An engineer is learning to write exploits in C++ and is using the exploit tool Backtrack. The engineer wants to compile the newest C++ exploit and name it calc.exe. Which command would the engineer use to accomplish this?
A circuit level gateway works at which of the following layers of the OSI Model?
Which of the following is a characteristic of Public Key Infrastructure (PKI)?
A developer for a company is tasked with creating a program that will allow customers to update their billing and shipping information. The billing address field used is limited to 50 characters. What pseudo code would the developer use to avoid a buffer overflow attack on the billing address field?
A network administrator received an administrative alert at 3:00 a.m. from the intrusion detection system. The alert was generated because a large number of packets were coming into the network over ports 20 and 21. During analysis, there were no signs of attack on the FTP servers. How should the administrator classify this situation?
When using Wireshark to acquire packet capture on a network, which device would enable the capture of all traffic on the wire?
Which of the following scanning tools is specifically designed to find potential exploits in Microsoft Windows products?
Which of the following is an example of IP spoofing?
One advantage of an application-level firewall is the ability to
When comparing the testing methodologies of Open Web Application Security Project (OWASP) and Open Source Security Testing Methodology Manual (OSSTMM) the main difference is
What is a successful method for protecting a router from potential smurf attacks?
Which NMAP command combination would let a tester scan every TCP port from a class C network that is blocking ICMP with fingerprinting and service detection?
After an attacker has successfully compromised a remote computer, what would be one of the last steps that would be taken to ensure that the compromise is not traced back to the source of the problem?
Ethereal works best on ____________.

