Which initial procedure should an ethical hacker perform after being brought into an organization?
A computer technician is using a new version of a word processing software package when it is discovered that a special sequence of characters causes the entire computer to crash. The technician researches the bug and discovers that no one else experienced the problem. What is the appropriate next step?
Which of the following techniques will identify if computer files have been changed?
Which of the following is a preventive control?
Which security control role does encryption meet?
How can rainbow tables be defeated?
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:
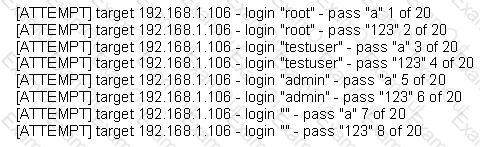
What is most likely taking place?
An NMAP scan of a server shows port 25 is open. What risk could this pose?
A company has publicly hosted web applications and an internal Intranet protected by a firewall. Which technique will help protect against enumeration?

