Smith is an IT technician that has been appointed to his company's network vulnerability assessment team. He is the only IT employee on the team. The other team members include employees from
Accounting, Management, Shipping, and Marketing. Smith and the team members are having their first meeting to discuss how they will proceed. What is the first step they should do to create the network
vulnerability assessment plan?
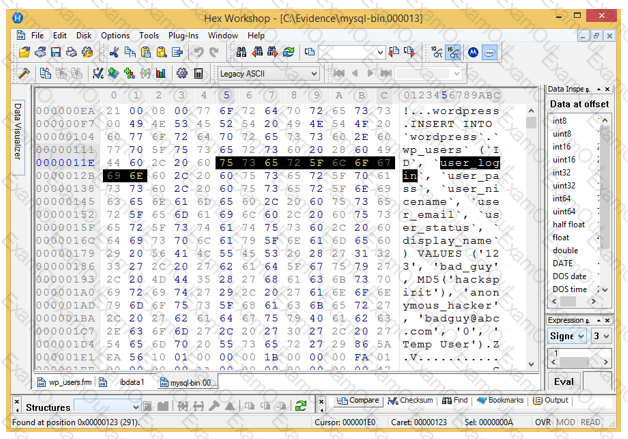
Analyze the hex representation of mysql-bin.000013 file in the screenshot below. Which of the following will be an inference from this analysis?
Buffer overflow vulnerabilities, of web applications, occurs when the application fails to guard its buffer properly and allows writing beyond its maximum size. Thus, it overwrites the _________. There are multiple forms of buffer overflow, including a Heap Buffer Overflow and a Format String Attack.
Which of the following Perl scripts will help an investigator to access the executable image of a process?
Which forensic investigation methodology believes that criminals commit crimes solely to benefit their criminal enterprises?
Which of the following registry hive gives the configuration information about which application was used to open various files on the system?
During forensics investigations, investigators tend to collect the system time at first and compare it with UTC. What does the abbreviation UTC stand for?
Which of these rootkit detection techniques function by comparing a snapshot of the file system, boot records, or memory with a known and trusted baseline?
What malware analysis operation can the investigator perform using the jv16 tool?
Checkpoint Firewall logs can be viewed through a Check Point Log viewer that uses icons and colors in the log table to represent different security events and their severity. What does the icon in the checkpoint logs represent?
Joshua is analyzing an MSSQL database for finding the attack evidence and other details, where should he look for the database logs?
Which of the following is found within the unique instance ID key and helps investigators to map the entry from USBSTOR key to the MountedDevices key?
Which of the following is a precomputed table containing word lists like dictionary files and brute force lists and their hash values?
Which of the following network attacks refers to sending huge volumes of email to an address in an attempt to overflow the mailbox or overwhelm the server where the email address is hosted so as to cause a denial-of-service attack?
Which Linux command when executed displays kernel ring buffers or information about device drivers loaded into the kernel?

