A small law firm located in the Midwest has possibly been breached by a computer hacker looking to obtain information on their clientele. The law firm does not have any on-site IT employees, but wants to search for evidence of the breach themselves to prevent any possible media attention. Why would this not be recommended?
In the following directory listing,
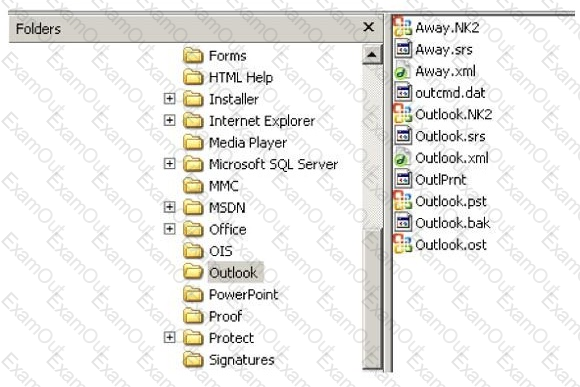
Which file should be used to restore archived email messages for someone using Microsoft Outlook?
Which of the following is NOT a part of pre-investigation phase?
Which of the following acts as a network intrusion detection system as well as network intrusion prevention system?
Cylie is investigating a network breach at a state organization in Florida. She discovers that the intruders were able to gain access into the company firewalls by overloading them with IP packets. Cylie then discovers through her investigation that the intruders hacked into the company phone system and used the hard drives on their PBX system to store shared music files. What would this attack on the company PBX system be called?
While looking through the IIS log file of a web server, you find the following entries:

What is evident from this log file?
A forensics investigator needs to copy data from a computer to some type of removable media so he can examine the information at another location. The problem is that the data is around 42GB in size. What type of removable media could the investigator use?
What is considered a grant of a property right given to an individual who discovers or invents a new machine, process, useful composition of matter or manufacture?
Billy, a computer forensics expert, has recovered a large number of DBX files during the forensic investigation of a laptop. Which of the following email clients can he use to analyze the DBX files?
What must be obtained before an investigation is carried out at a location?
What does the part of the log, “% SEC-6-IPACCESSLOGP”, extracted from a Cisco router represent?
What is the primary function of the tool CHKDSK in Windows that authenticates the file system reliability of a volume?
When marking evidence that has been collected with the aa/ddmmyy/nnnn/zz format, what does the nnn denote?
Preparing an image drive to copy files to is the first step in Linux forensics. For this purpose, what would the following command accomplish?
dcfldd if=/dev/zero of=/dev/hda bs=4096 conv=noerror, sync
Steven has been given the task of designing a computer forensics lab for the company he works for. He has found documentation on all aspects of how to design a lab except the number of exits needed. How many exits should Steven include in his design for the computer forensics lab?

