During an assessment of a web application, a penetration tester would like to test the application for blind SQL injection. Which of the following techniques should the penetration tester perform next?
A client claims that a ransomware attack has crippled its corporate network following a penetration test assessment. Which of the following is the most likely root cause of this issue?
Which of the following is most important to include in the final report of a static application-security test that was written with a team of application developers as the intended audience?
A penetration testing firm performs an assessment every six months for the same customer. While performing network scanning for the latest assessment, the penetration tester observes that several of the target hosts appear to be residential connections associated with a major television and ISP in the area. Which of the following is the most likely reason for the observation?
Which of the following describes how a penetration tester could prioritize findings in a report?
Which of the following documents should be consulted if a client has an issue accepting a penetration test report that was provided?
Which of the following tools would be best to use to conceal data in various kinds of image files?
During a vulnerability scanning phase, a penetration tester wants to execute an Nmap scan using custom NSE scripts stored in the following folder:
/home/user/scripts
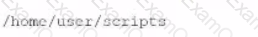
Which of the following commands should the penetration tester use to perform this scan?
Given the following table:
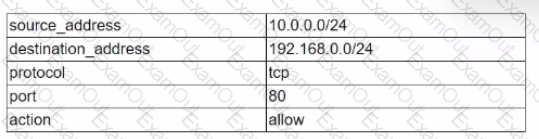
Which of the following data structures would most likely be used to store known-good configurations of firewall rules in a Python script?
During a client engagement, a penetration tester runs the following Nmap command and obtains the following output:
nmap -sV -- script ssl-enum-ciphers -p 443 remotehost
| TLS_ECDHE_ECDSA_WITH_RC4_128_SHA
| TLS_ECDHE_RSA_WITH_RC4_128_SHA
TLS_RSA_WITH_RC4_128_SHA (rsa 2048)
TLS_RSA_WITH_RC4_128_MD5 (rsa 2048)
Which of the following should the penetration tester include in the report?

