A penetration tester is testing a new API for the company's existing services and is preparing the following script:
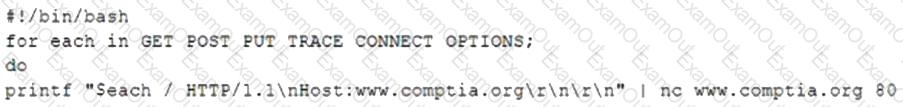
Which of the following would the test discover?
A penetration tester found several critical SQL injection vulnerabilities during an assessment of a client's system. The tester would like to suggest mitigation to the client as soon as possible.
Which of the following remediation techniques would be the BEST to recommend? (Choose two.)
When planning a penetration-testing effort, clearly expressing the rules surrounding the optimal time of day for test execution is important because:
A penetration tester is conducting an engagement against an internet-facing web application and planning a phishing campaign. Which of the following is the BEST passive method of obtaining the technical contacts for the website?
Which of the following assessment methods is MOST likely to cause harm to an ICS environment?
A client would like to have a penetration test performed that leverages a continuously updated TTPs framework and covers a wide variety of enterprise systems and networks. Which of the following methodologies should be used to BEST meet the client's expectations?
A penetration tester has prepared the following phishing email for an upcoming penetration test:

Which of the following is the penetration tester using MOST to influence phishing targets to click on the link?
During an assessment, a penetration tester obtains a list of 30 email addresses by crawling the target company's website and then creates a list of possible usernames based on the email address format. Which of the following types of attacks would MOST likely be used to avoid account lockout?
A penetration tester utilized Nmap to scan host 64.13.134.52 and received the following results:
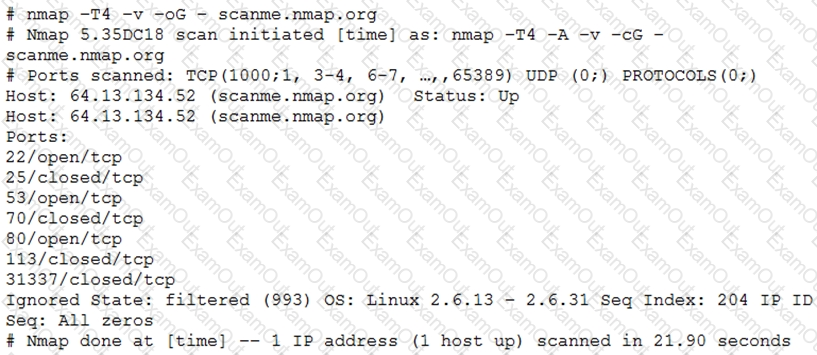
Based on the output, which of the following services are MOST likely to be exploited? (Choose two.)
A security analyst needs to perform a scan for SMB port 445 over a/16 network. Which of the following commands would be the BEST option when stealth is not a concern and the task is time sensitive?

