Which of the following protocols is commonly associated with TCP port 443?
A network administrator is unable to ping a remote server from a newly connected workstation that has been added to the network. Ping to 127.0.0.1 on the workstation is failing. Which of the following should the administrator perform to diagnose the problem?
Which of the following panels would be best to facilitate a central termination point for all network cables on the floor of a company building?
Which of the following attacks forces a switch to send all traffic out of all ports?
Which of the following is enforced through legislation?
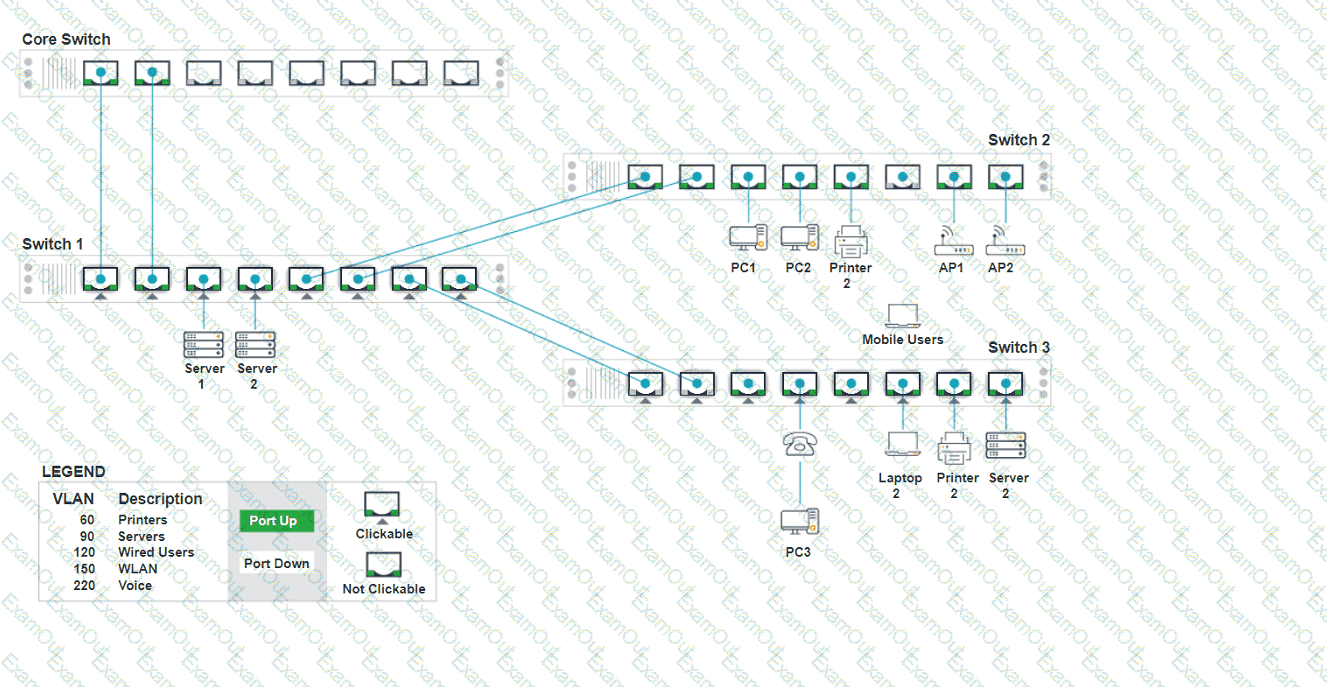
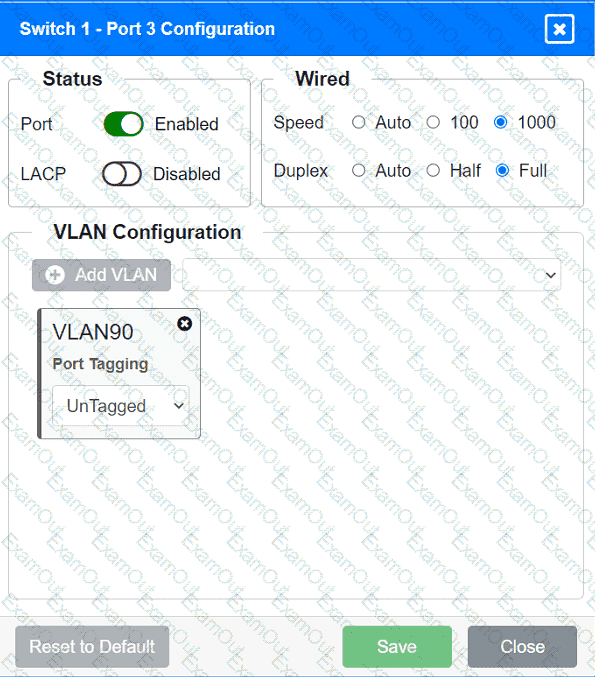
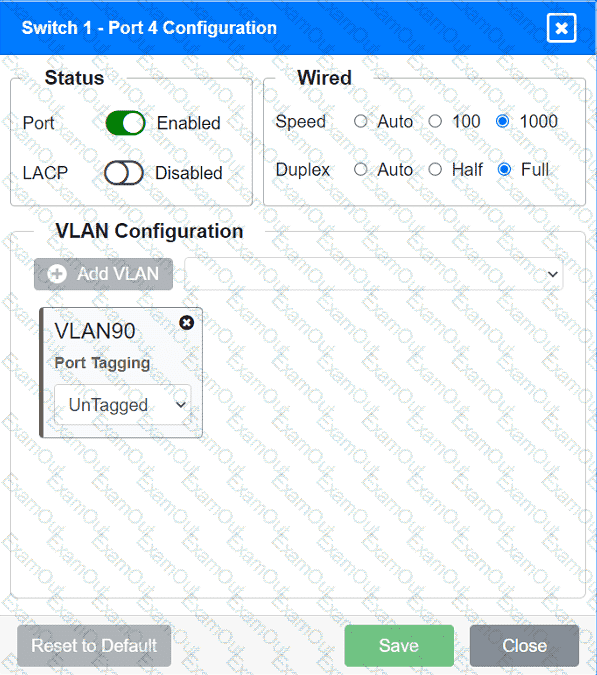
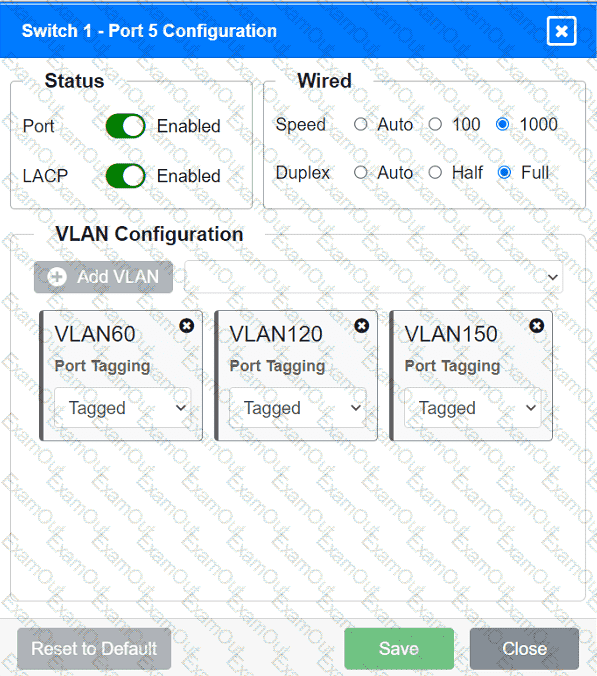
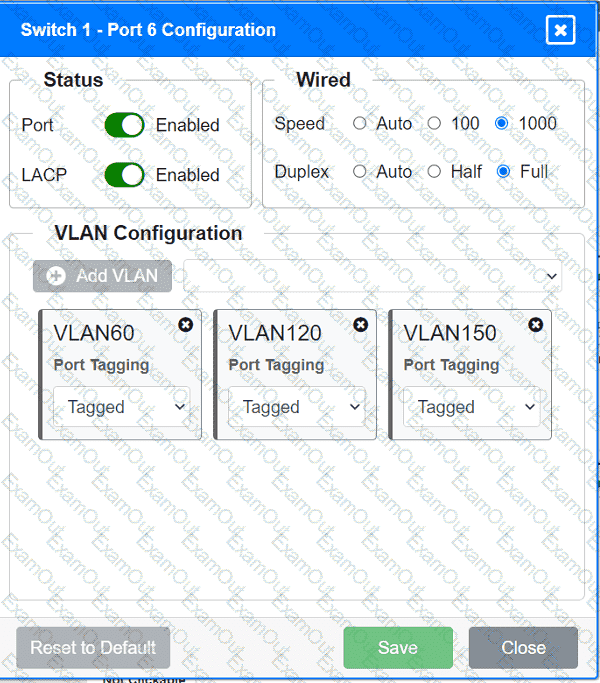
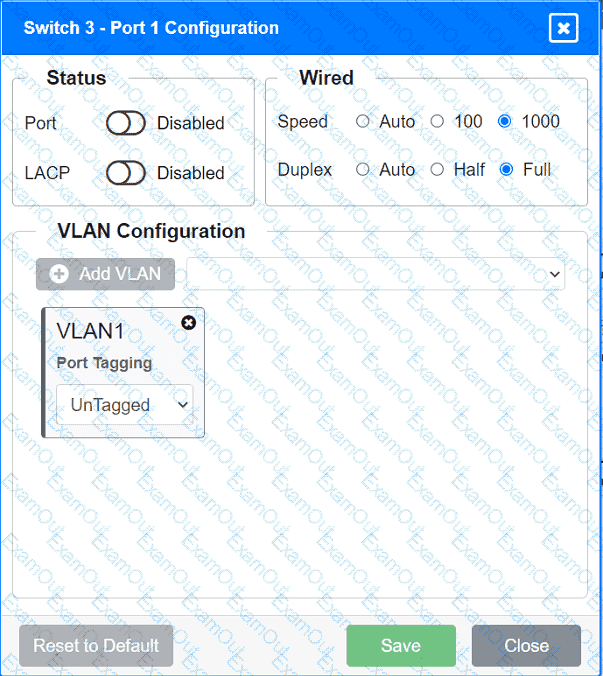
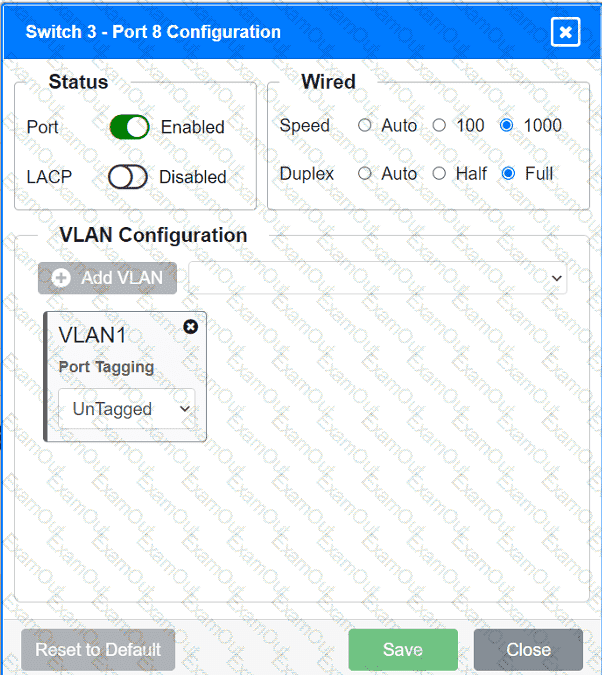
A network technician replaced an access layer switch and needs to reconfigure it to allow the connected devices to connect to the correct networks.
INSTRUCTIONS
Click on the appropriate port(s) on Switch 1 and Switch 3 to verify or reconfigure the
correct settings:
· Ensure each device accesses only its
correctly associated network.
· Disable all unused switchports.
. Require fault-tolerant connections
between the switches.
. Only make necessary changes to
complete the above requirements.
A network administrator upgraded the wireless access points and wants to implement a configuration that will give users higher speed and less channel overlap based on device compatibility. Which of the following will accomplish this goal?
A network administrator needs to connect a department to a new network segment. They need to use a DHCP server located on another network. Which of the following can the administrator use to complete this task?
A newly opened retail shop uses a combination of new tablets, PCs, printers, and legacy card readers. Which of the following wireless encryption types is the most secure and compatible?
Which of the following is the most cost-effective way for a network administrator to establish a persistent, secure connection between two facilities?

