A user logs into a laptop using a username and complex password. This is an example of:
Which of the following is the slowest processing speed?
A user opens an application that is installed locally on a PC. The application connects directly to a database that is located on a server in a data closet in the same building. Which of the following application architecture models does this describe?
Which of the following is the equivalent of 1 KB?
Which of the following tasks is typically performed during the identification phase of the troubleshooting
methodology?
A company purchased a software program. The EULA states that the software can be installed on as many computers as the company wants, but only four users can be using the software at any point in time. Which of the following types of licenses is this an example of?
An employee is asked to generate a report on a student information system. The employee uses spreadsheet software and connects to a remote database to pull data for the report. Which of the following types of
application architectures did the employee use?
Given the following pseudocode:
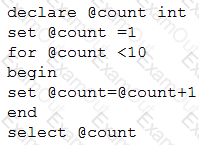
Which of the following is the output of the code?
A technician is configuring a new Windows PC and needs to choose a filesystem that supports encryption. Which of the following is the technician most likely to choose?
Joe, a user, finds out his password for a social media site has been compromised. Joe tells a friend that his email and banking accounts are probably also compromised. Which of the following has Joe MOST likely performed?

