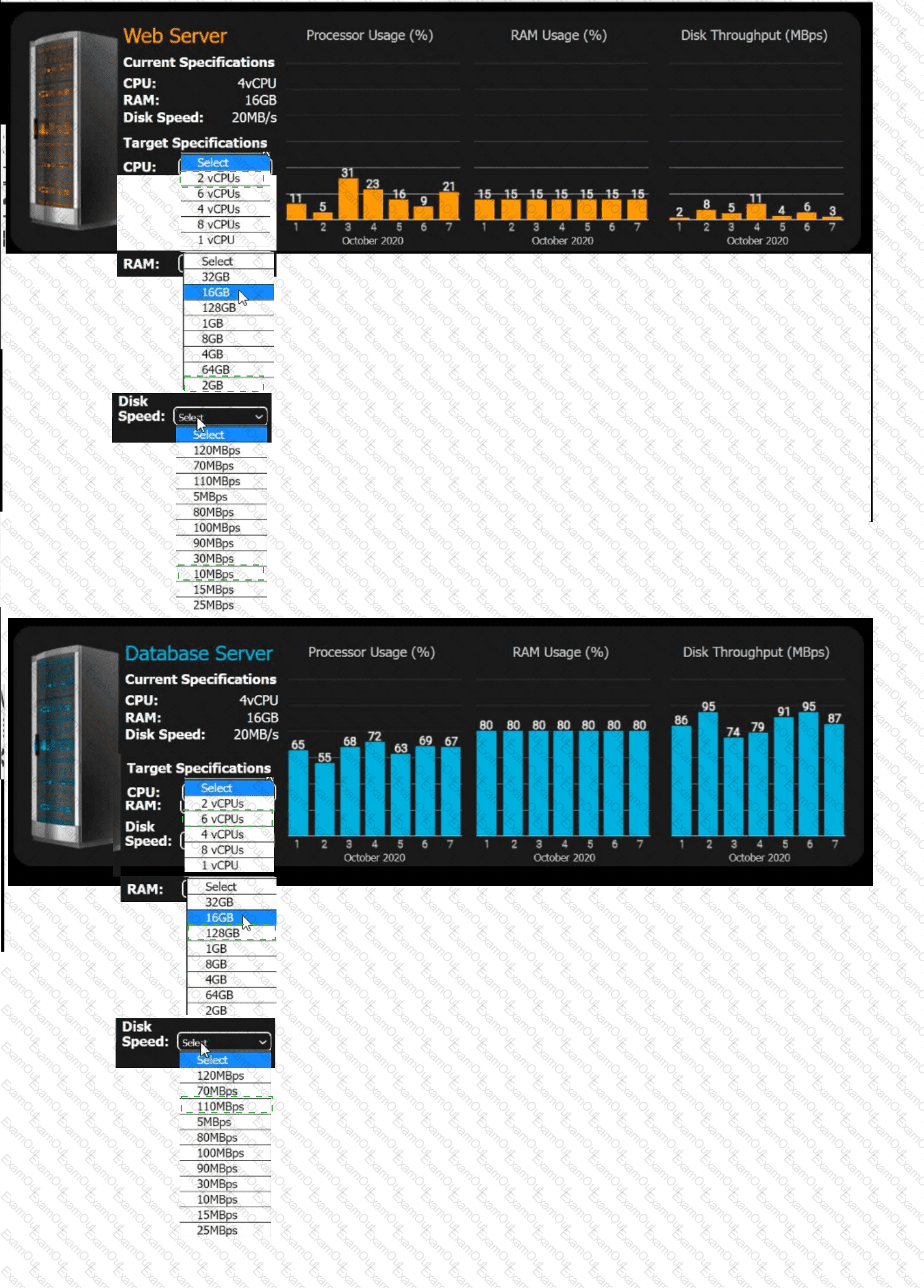
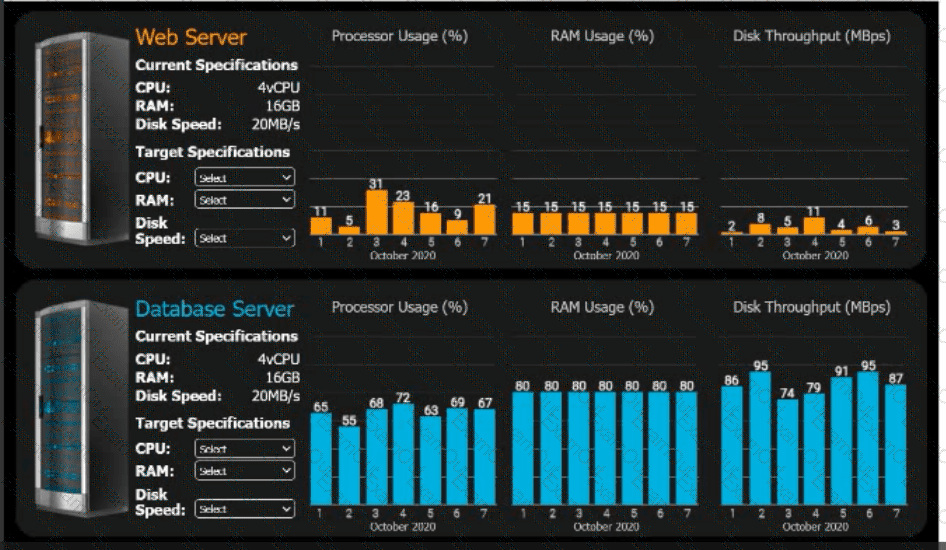
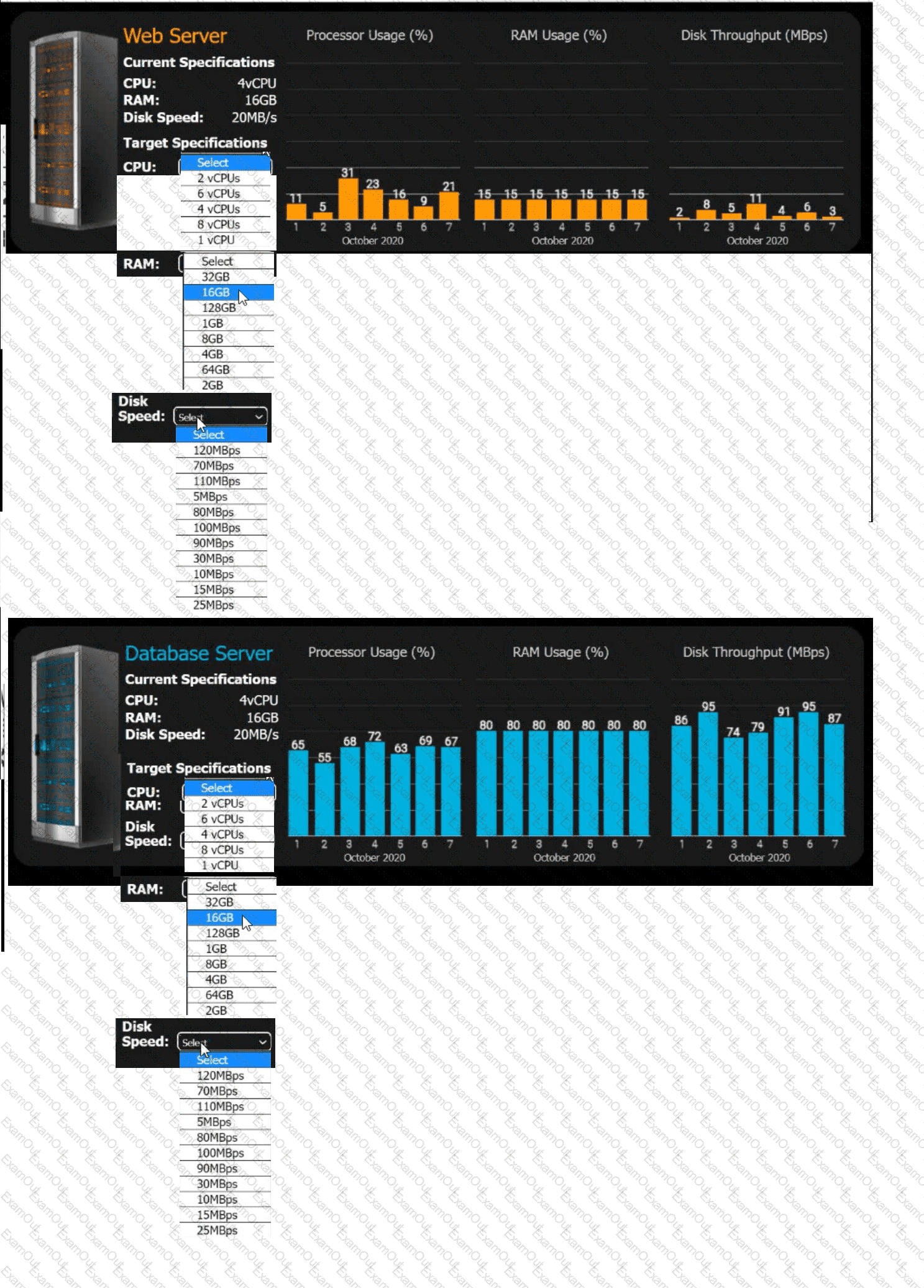
An e-commerce company is migrating from an on-premises private cloud environment to
a public cloud IaaS environment. You are tasked with right-sizing the environment to
save costs after the migration. The company's requirements are to provide a 20% overhead above the average resource consumption, rounded up.
INSTRUCTIONS
Review the specifications and graphs showing resource usage for the web and database servers. Determine the average resource usage and select the correct specifications from the available drop-down options.
Which of the following is true of SSDs?
A cloud engineer is in charge of deploying a platform in an laaS public cloud. The application tracks the state using session cookies, and there are no affinity restrictions. Which of
the following will help the engineer reduce monthly expenses and allow the application to provide the service?
A developer is sending requests to a SaaS application. The developer becomes unable to send more requests after sending a number of them, but other developers can still send requests. Which of the following is most likely causing the issue?
Users report being unable to access an application that uses TLS 1.1. The users are able to access other applications on the internet. Which of the following is the most likely
reason for this issue?
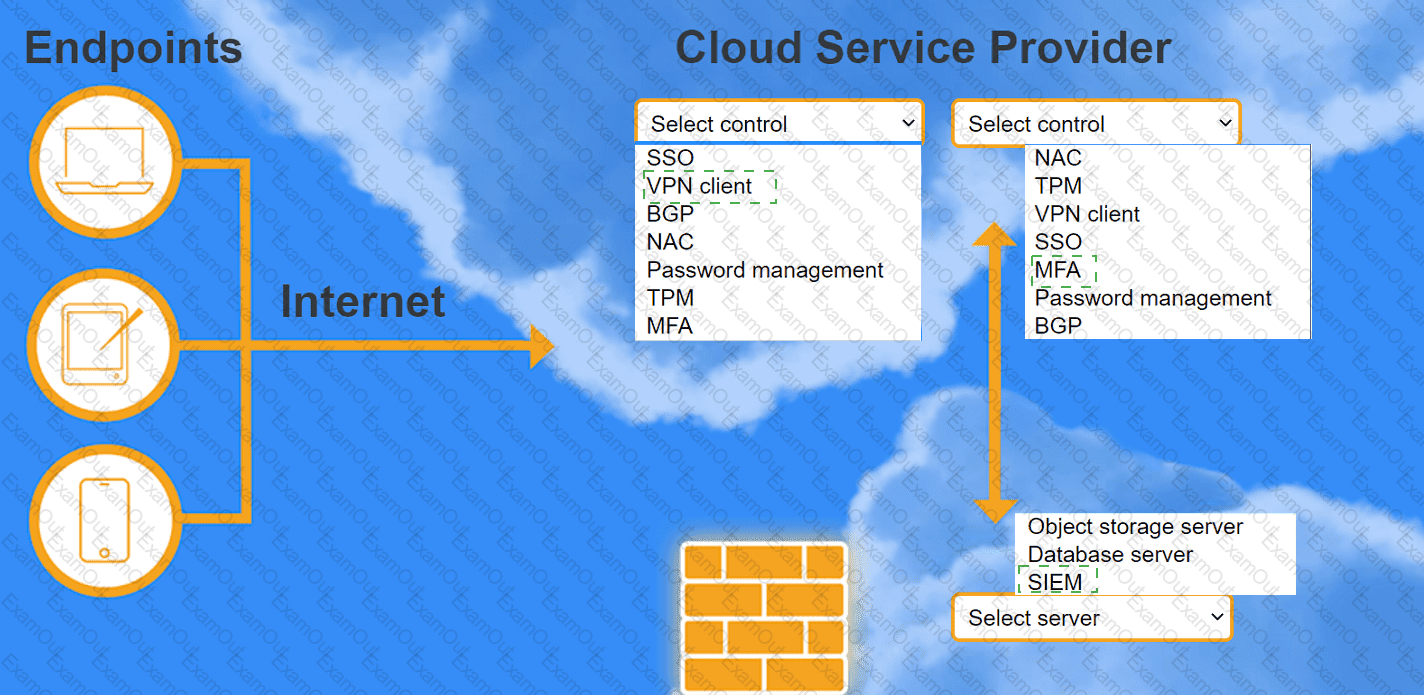
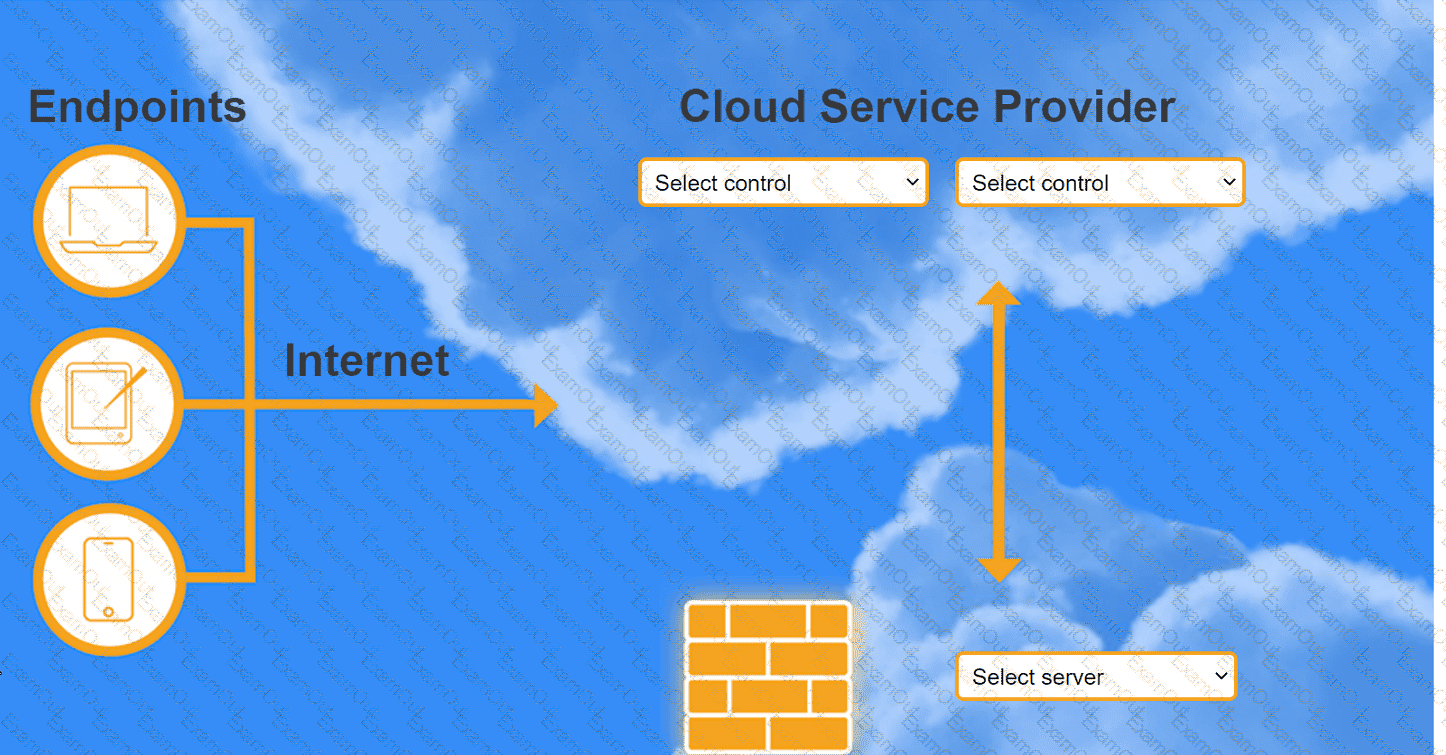
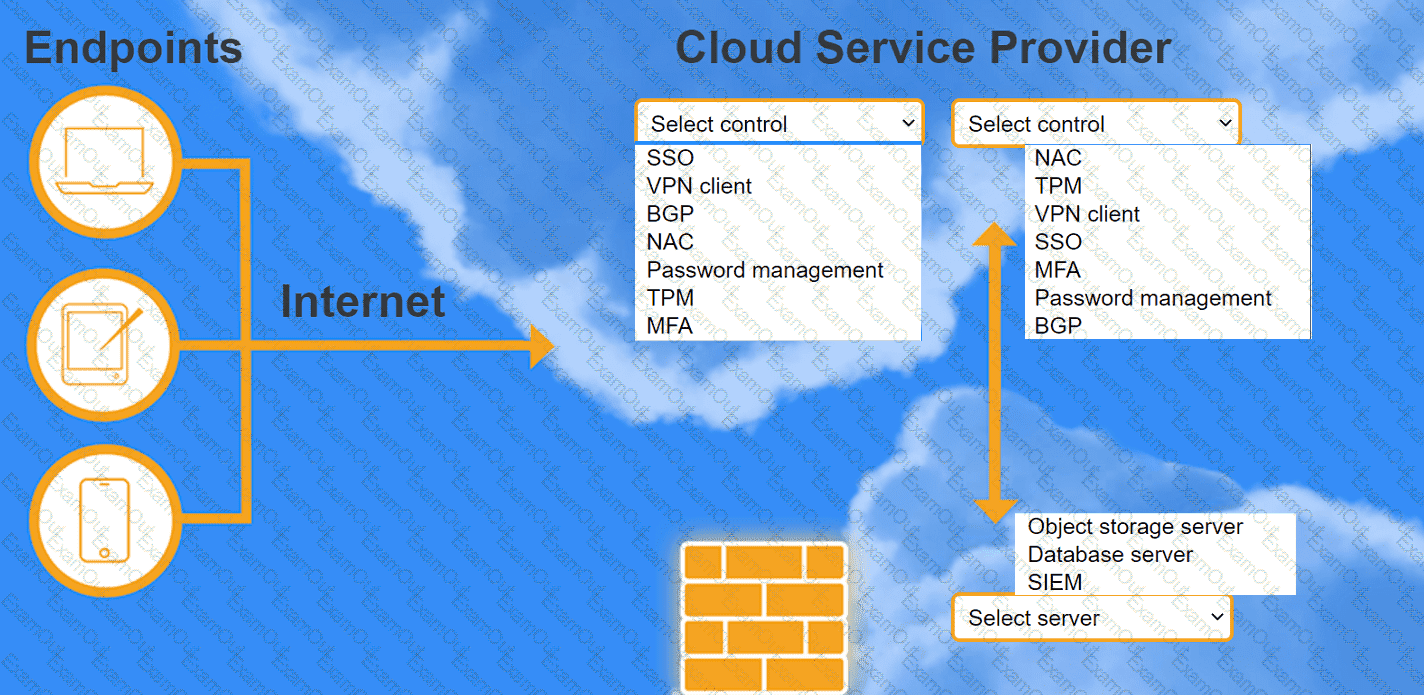
A highly regulated business is required to work remotely, and the risk tolerance is very low. You are tasked with providing an identity solution to the company cloud that includes the following:
secure connectivity that minimizes user login
tracks user activity and monitors for anomalous activity
requires secondary authentication
INSTRUCTIONS
Select controls and servers for the proper control points.
A company developed an online trading platform. The engineering team selected event-based scaling for the platform's underlying resources. The platform resources scale up with every 2,000 subscribed users. The engineering team finds out that although compute utilization is low, scaling is still occurring. Which of the following statements best explains why this is the case?
An IT manager needs to deploy a cloud solution that meets the following requirements:
. Users must use two authentication methods to access resources.
· Each user must have 10GB of storage space by default.
Which of the following combinations should the manager use to provision these requirements?
A software engineer at a cybersecurity company wants to access the cloud environment. Per company policy, the cloud environment should not be directly accessible via the internet. Which of the following options best describes how the software engineer can access the cloud resources?
An on-premises data center is located in an earthquake-prone location. The workload consists of real-time, online transaction processing. Which ot the following data protection strategies should be used to back up on-premises data to the cloud while also being cost effective?